PF_RING FT
Fast, Assisted Flow Processing and L7 Classification
Most Network monitoring and security applications are based on flow processing, that includes packet capture, decoding and classification. PF_RING is a flexible framework that can be used to accelerate the packet capture, leveraging on PF_RING ZC drivers or specialized adapters, and extract packet metadata. This let the application focus on packet processing, rather than dealing with packet capture and packet parsing, while running with the best performance.
PF_RING FT is taking one step further, it assists any flow processing application in the packet classification activity. PF_RING FT implements a flow table that can be used to keep track of flows and provides many hooks to be able to customize and extend it for building any type of application on top of it, including probes, IDSs, IPSs, L7 firewalls.
Although PF_RING FT is distributed with PF_RING, it is possible to use the library with any third-party packet capture framework (including Libpcap and DPDK), as its data-ingestion API is capture-agnostic.
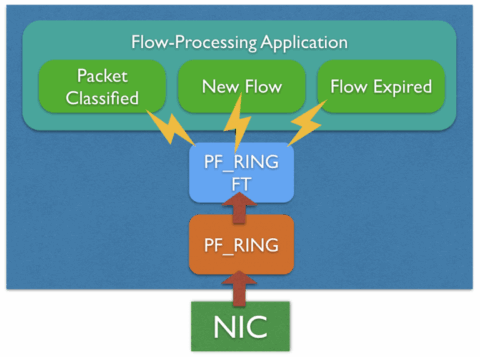
at a glance
Key Features
- High-performance generation of flow records (NetFlow/IPFIX-like) directly from live traffic
- Programmable flow processing with configurable flow aging
- Built-in Deep Packet Inspection (DPI) via nDPI to classify protocols and applications
- Flexible export format, flows can be exported in any format
- Efficient use of multi-core systems with NUMA awareness
- Easy integration with zero-copy packet processing frameworks like PF_RING ZC
- Low resource footprint, designed for high-throughput with minimal CPU and memory usage
Ideal for Every Environment
Use Cases
Develop a High-Speed NetFlow Probe
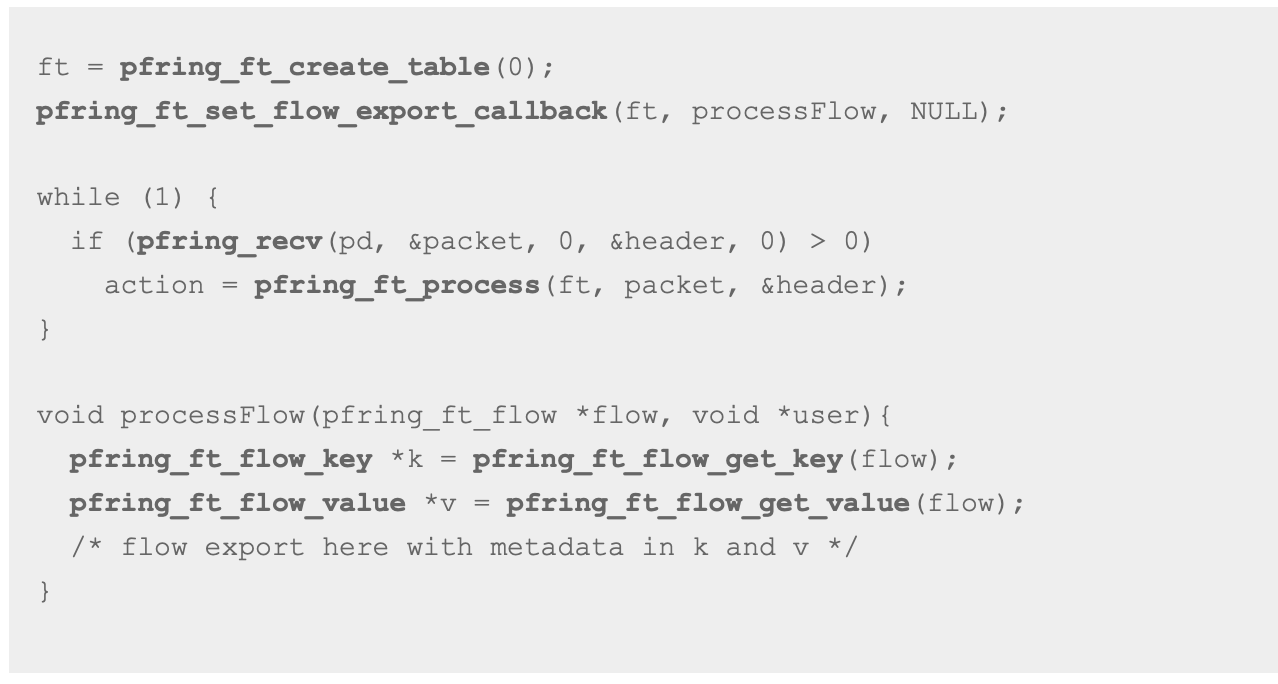
Designing and implementing a flow processing application on top of PF_RING FT is quite straightforward as it provides a clean API that can be used to do complex things in a few lines of code. The following code snippet shows how it is easy to capture traffic and export flow informations with PF_RING FT. For a full code example have a look at the demo applications available in PF_RING. For more information please refer to the guide and API documentation.
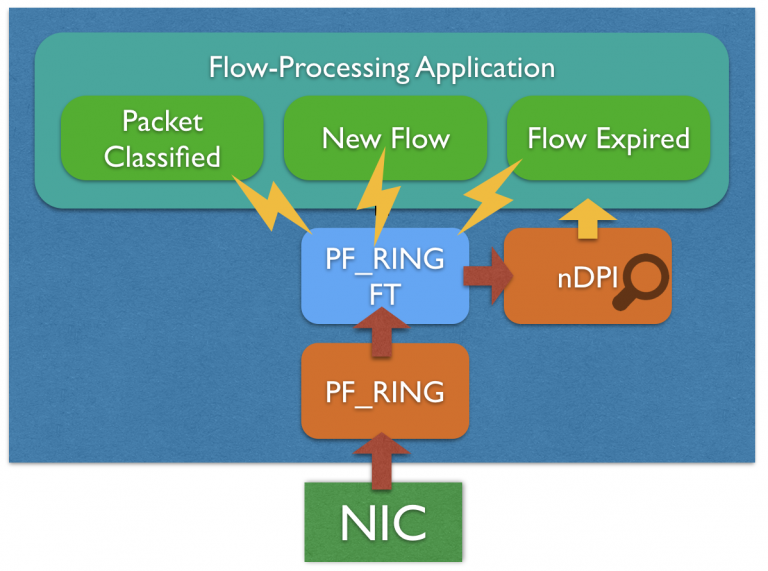
Layer-7 Traffic Classification with nDPI
PF_RING FT is natively integrated with nDPI for providing L7 protocol informations out of the box. The application itself does not need to deal with the nDPI library directly as everything happens behind the scenes, getting the L7 protocol is just as easy as enabling L7 detection through the API and reading the L7 protocol from the flow metadata. In addition to protocol detection, PF_RING FT also categorizes the traffic leveraging the nDPI categories, extracts metadata, detects flow risks.
Application Filtering and Shunting
PF_RING FT features a L7 filtering engine that can be used by inline applications for filtering flows based on the application protocol. In addition to the built-in filtering engine, the application can mark flows for filtering or shunting them based on custom policies.
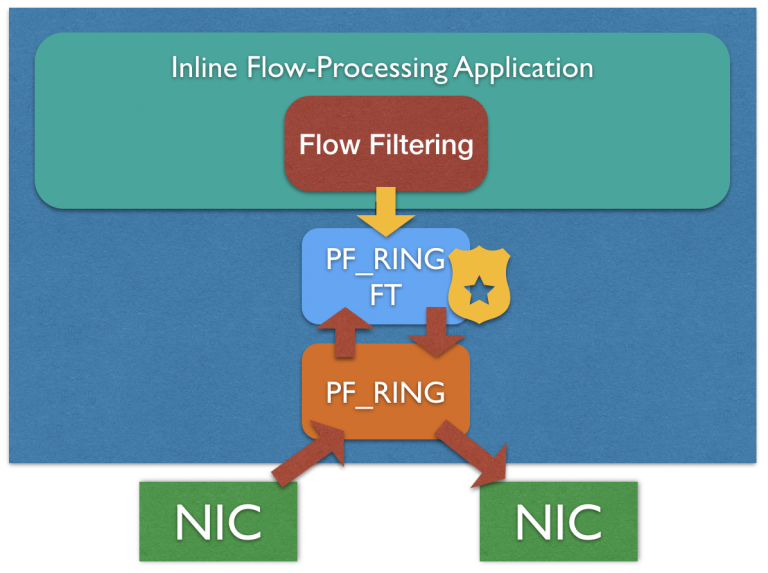
IDS/IPS Acceleration
The PF_RING FT Layer-7 filtering engine can also be used for accelerating CPU-bound applications, such as IDS/IPSs including Suricata, Bro and Snort, shunting flows based on the application protocol. Discarding elephant flows is becoming a common yet effective practice for reducing the amount of traffic an IDS/IPS need to inspect (typically multimedia traffic), dramatically reducing packet loss and improving the system performance.
Suricata has native support (bypass) for shunting elephant flows using eBPF, this means that the application is injecting filtering rules (5-tuples) in kernel space as soon as an elephant flow is detected. This approach has come limitations: it requires a ruleset in Suricata able to detect all multimedia protocols, packet parsing is not flexible as eBPF programs cannot loop (it does not work with encapsulations, including vlan and QinQ), it cannot keep flow state (making it complicated to handle flows expiration).
Leveraging on PF_RING FT, a PF_RING-based or Libpcap-based application can take advantage of L7 shunting without changing a single line of code. Since PF_RING FT is based on nDPI for protocols detection, filtering multimedia traffic mens just listing the protocol names in a configuration file. More information for accelerating Suricata or other IDSs can be found in the User’s Guide.
Specifications
Tech Specs
- Linux
- C API compatible with PF_RING, PF_RING ZC, libpcap, DPDK
x86 64-bit CPU (Intel and AMD)
- Ethernet
- IPv4/IPv6
- TCP/UDP/ICMP
- GTP/GRE/MPLS/VXLAN/PPP
- 450+ Layer-7 application protocols supported by nDPI
