After over one year of work, we’re proud to announce you that ntopng 4.0 is finally out. In this time we have redesigned ntopng for speed and openness, by breaking apart the existing monolithic C++ engine into a Lua-scriptable micro-engine. This is to enable people to contribute to the project without them being scared of coding in C++.
The major breakthroughs we have brought with this release are:
- A plugin engine that allows anyone with some basic Lua coding skills to tap straight into every single flow, host, or other network element and perform custom actions such as the triggering of alerts
- A fresh graphical user interface, featuring new icons, a refreshed look and feel, and light/dark themes
- The active monitoring of hosts Round Trip Times (RTTs) for HTTP, HTTPS, ICMP and ICMPv6
- Many cybersecurity-related features, including SSH and TLS fingerprinting, TLS analysis and alerting, and Suricata events integration
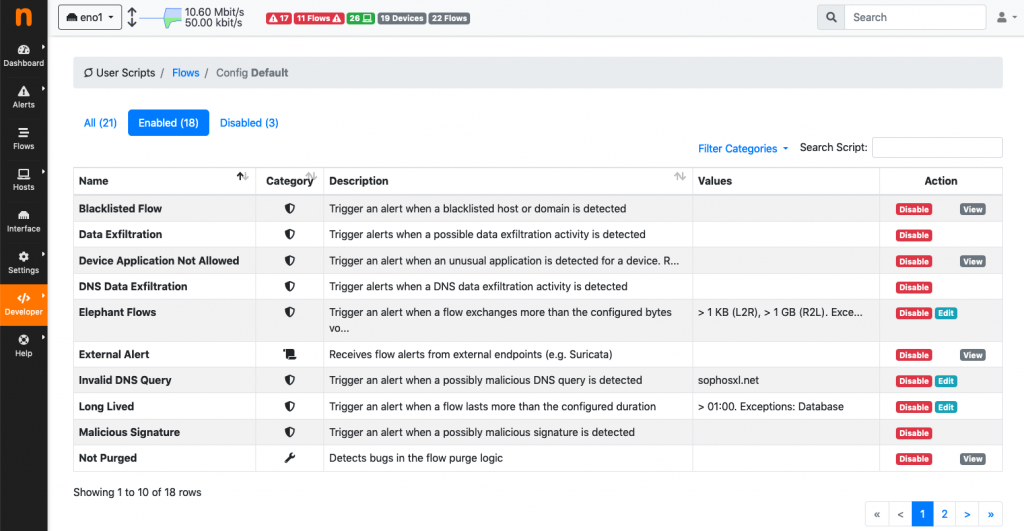
The plugin engine is probably most important breakthrough of v4: all the entities (e.g. flows, hosts, networks, SNMP…) are now driven by scripts that are executed based upon events. A typical event is a new flow dissected, a SNMP polling session, or a host just appeared on the network. Scripts can perform actions (e.g. monitor RTT of selected hosts issuing periodic ping) or trigger alerts based on thresholds or severity reported by the score. More in detail:
- Flows: flow plugins execute when a new flow is detected, when it’s been active for a certain time, or when it’s gone idle. Want to create an alert as soon as a flow is found to be going to a suspicious country? Need to detect Dropbox flows that are transferring too much data or outside business hours? Those are just a couple of things that can be done with flow plugins!
- Hosts: host plugins execute periodically on all active hosts. This allows anyone to create custom actions of virtually any kind. For example, host plugins can be written to detect hosts that are doing too much traffic, or to spot those that are probing the network with SYN scans, just to name a few.
- Other network elements: other plugins can be executed for instance when an interface is dropping too many packets, when the load of the system on top of which is running ntopng exceeds a given threshold, or when an interface of an SNMP device goes down, among many others.
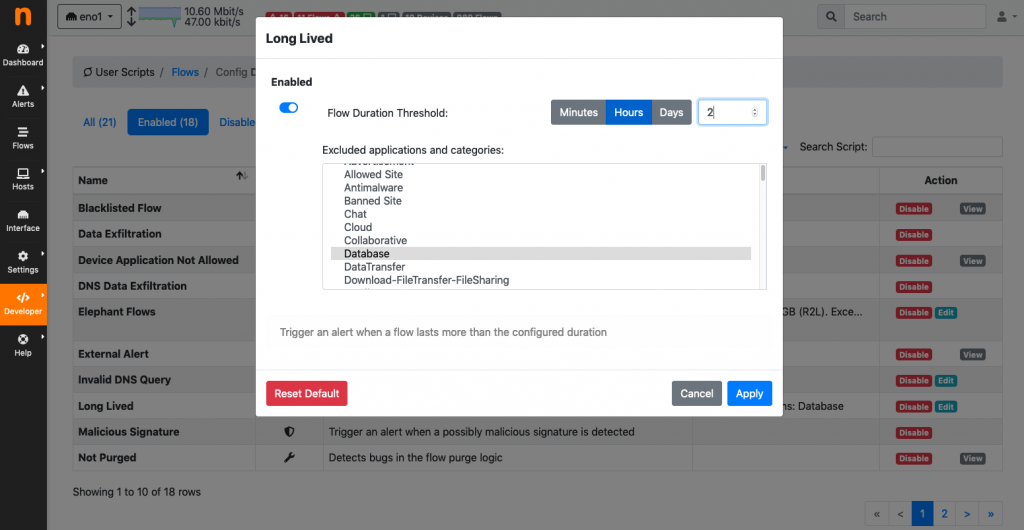
Everything happens through the GUI: enable/disable/view source code / set alarm thresholds. You can read more in the development section of the user’s guide for developing your own plugin.
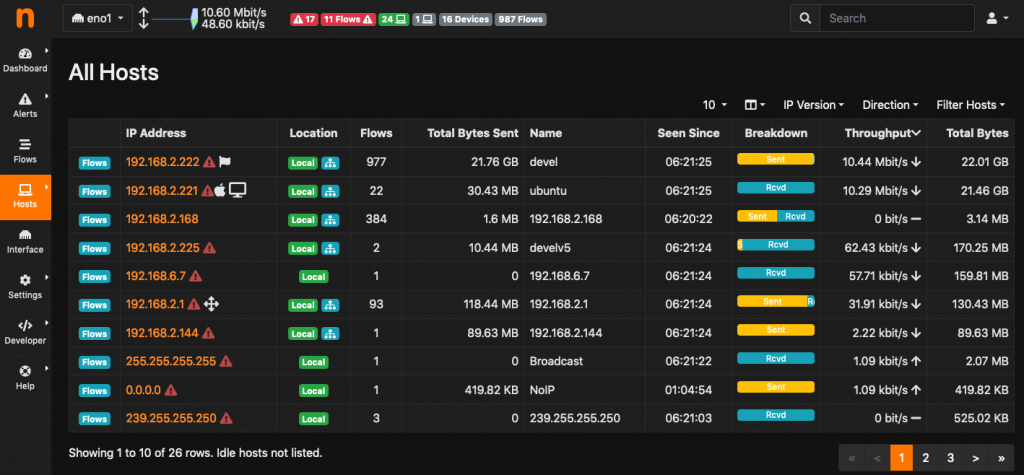
As you can have noticed from the screenshots above, v4 has a new, responsive look and feel. The navigation bar has been moved from the top to the left of the page to optimally use the space available on wide screens which are common today. In addition, the status bar, which was previously placed at the bottom of the page, has been moved to the top, to make the essential ntopng status information always visible and available to the user. The user interface is now skinnable through themes, including a dark theme designed to reduce eyestrain to those that spend a lot of time in front of the screen.
As previously said, we have decided to enrich ntopng with new cybersecurity-oriented features mostly based on the work we have done on nDPI. In particular, 4.0 features SSH fingerprinting with hassh, TLS fingerprinting with JA3. Fingerprints are good indicators for good/bad traffic, especially today where the traffic is encrypted and thus it is increasingly difficult to understand it. Check out “Effective TLS Fingerprinting Beyond JA3” and “How Encryption Changed Network Traffic (Monitoring). Finally.” for extra information. TLS is not only fingerprinted, it is also thoroughly analyzed to check (and alert) when invalid, expired or mismatched certificates are detected or when certain cipher suites are weak. Everything about the TLS analysis is explained in the article “TLS/SSL Analysis: When Encryption and Safety Are Not Alike“. In terms of security, v4.0 can also easily be connected with Suricata for unprecedented visibility into traffic and security events!
Another new feature of v4 is the ability to actively monitor hosts latencies (aka RTT, round trip time): we’re complementing traditional passive traffic monitoring with active probing for keeping track of selected relevant assets. Currently, RTT probes are available for HTTP, HTTPS, ICMP and ICMPv6 and allow the user to quantify hosts RTT, and receive alerts when anomalous RTT values are detected or when monitored hosts become unreachable.
A comprehensive list of changes introduced in this major release is available in the changelog. As usual, ntopng installation instructions are available at packages.ntop.org. Try and experiment it, suggestions and contributions are very welcome! And why not joining us on our official telegram channel @ntop_community?
This release has been a major effort, and we expect people to contribute with plugins and scripts. We aim at creating a single comprehensive tool for network security and visibility. Hope to see your pull requests soon on GitHub.
Enjoy!