Suppose that you are travelling abroad and you need to access some Internet sites that are not available abroad. Or suppose that you want to evade the restrictions of your ISP, of the hotel room where you are currently staying, or the WiFi hotspot you are using for connecting to the Internet. The simplest thing to do is to open a VPN and you’re done. However VPNs are not very flexible and they require a single place where everybody meet and great. n2n instead is based on the peer-to-peer paradigm and it implements an adaptable network overlay that you can use to access your private assets, regardless of their actual location.
Ingredients:
- A host with a public IP (or at least a static NAT for publishing the supernode port to the Internet) that can act as supernode.
- A host sitting on a network back to your home country: it can be deployed on the same host where the supernode is running, or somewhere else. This host (that will run the n2n edge component) will act as router for your Internet traffic. A Raspberry PI is perfectly adequate for running both the the supernode and the edge.
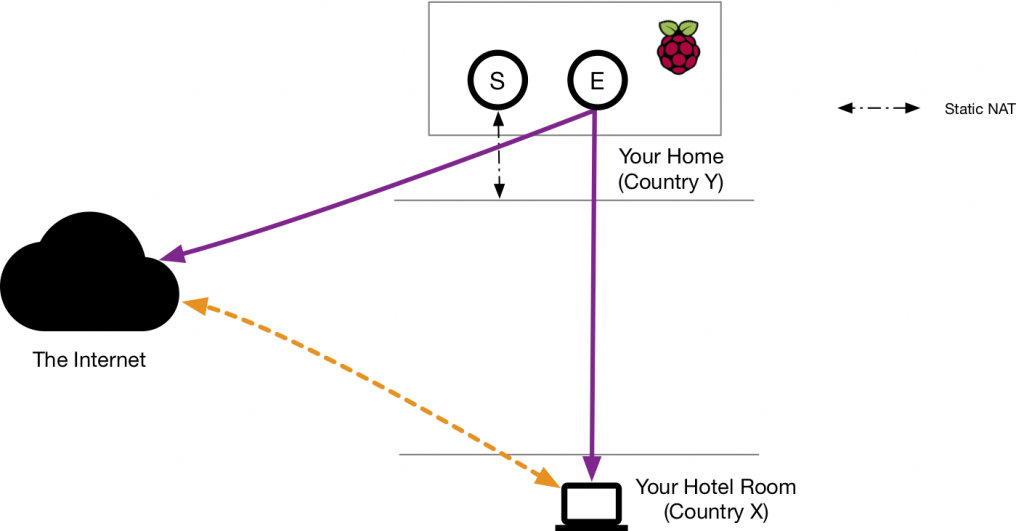
As you can see from the above picture, the goal of this exercise is to exit the Internet though the purple path (and thus from your home network) rather than from your hotel room. This way you can evade the restrictions (orange path) of the hotel Internet provider, as well be visible using a home country IP rather than using the remote hotel room IP.
The home Raspberry (connected to the Internet via eth0) should be configured with NAT to mask the remote host IP.
edge -d n2n0 -c mynetwork -k mypassword -u 99 -g 99 -m DE:AD:BE:EF:91:10 -a 192.168.254.6 -p 50001 -l myPublicIP:9876 -r iptables --table nat --delete-chain iptables --table nat --append POSTROUTING --out-interface eth0 -j MASQUERADE iptables --append FORWARD --in-interface n2n0 -j ACCEPT iptables -A FORWARD -i eth0 -o n2n0 -j ACCEPT
In essence it creates a new n2n0 interface that will NAT all the ingress traffic and let you access the Internet though the Raspberry.
On the PC/Mac laptop of you use on your hotel room you can do (we assume that the local gateway is 192.168.2.1):
# edge -d n2n0 -c mynetwork -k mypassword -u 99 -g 99 -m DE:AD:BE:EF:91:10 -a 192.168.254.20 -p 50001 -l myPublicIP:9876 -r # route del default # route add myPublicIP/32 gw 192.168.2.1 # route add default gw 192.168.254.6
In essence you use the local Internet connectivity only for accessing the supernode, and all the rest of the traffic will pass though the n2n tunnel.
You can verify the IP address you as using to access the Internet using services like ipinfo.io and you will see that the Internet believes you’re no longer abroad, but back home. In future n2n version we will reduce the number of parameters as well auto-configure routing to make all this even simpler.
Enjoy!