In this post Martin shows how he has used ntopng to detect Qakbot trojan. Many thanks for this contribution.
Introduction
I am using ntopng for network monitoring quite some time now and I was curios to see, what ntopng would alert when detecting malware.
The website malware traffic analysis is a great source for malware captured in network traffic. I decided to take a Qakbot infection with spambot activity [1]. From the pcap file name we see to expect
- Qakbot, a active [2] banking trojan [3]
- Cobalt Strike, a commercial penetration testing tool, unfortunately pirated versions of Cobalt Strike have been leaked [4]
- Spambot activity, distributing QakBot
- Further I used a tutorial how to examine Qakbot infections with Wireshark from Unit42 [5].
For the analysis I setup a virtual machine with Ubuntu Server 20.04 LTS and installed the current ntopng nightly build [6], using the community license.
Ntopng per default is built for continuous network monitoring, but directing the interface to a pcap, it can read and process it.
Analysis
To start ntopng sudo is needed, followed by the -i for interface or pcap file:
sudo ntopng -i 2020-12-07-Qakbot-with-Cobalt-Strike-and-spambot-activity.pcap
The web gui can be reached over
http://localhost:3000 or http://<server ip>:3000
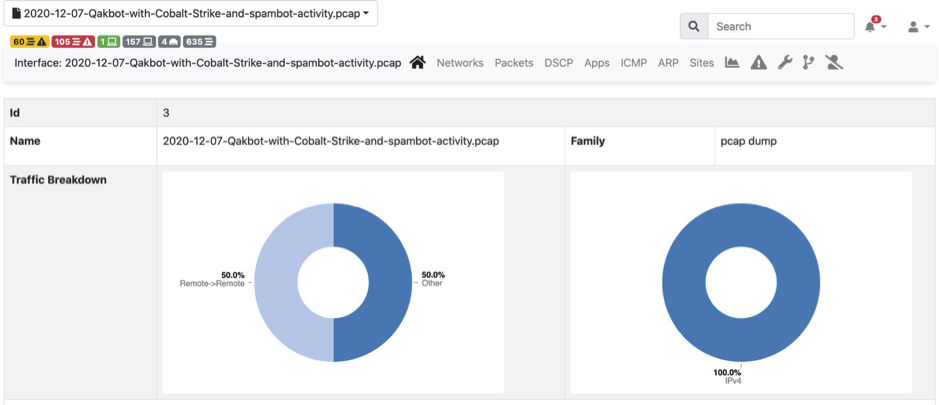
Ntopng will prompt for username and password and you will have to select a new admin password. Once logged in, you will see the interface overview, showing that the selected interface is a pcap dumb and the name of the pcap file:
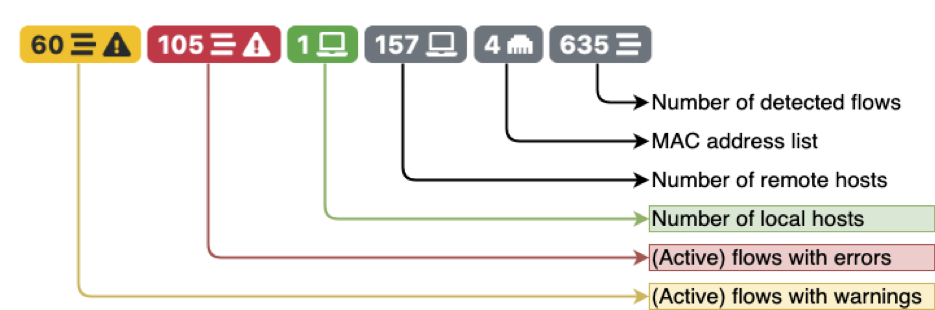
A quick look at the traffic summary icons reveal lots of work ahead, and many problems are being identified:
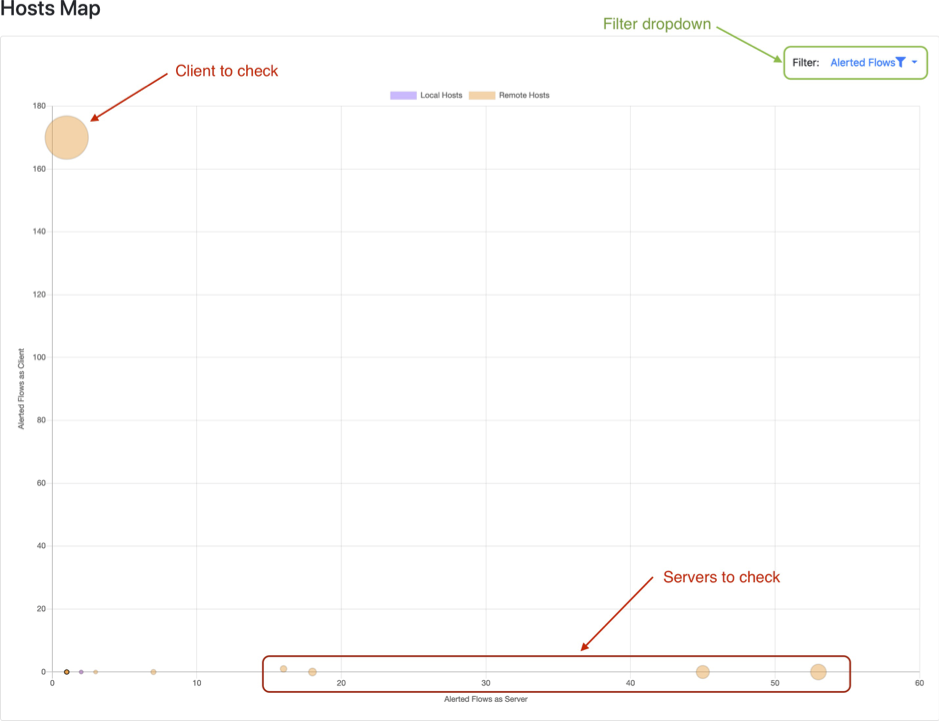
Now rather than checking out the flow warnings or errors, I navigate to the “Host Map” from the Maps menu and select “Alerted Flows” in the dropdown filter menu. This view gives a fast overview of hosts with alerts. The hosts map shows on the x-axis hosts identified as servers with alerts and in the y-axis host identified as clients. Note: a host can a be a server and/or a client. The size of the circles is proportional with the number of alerts, i.e. the biggest circle shows the host with the most alerts. In the filter dropdown you can find other useful filters, like “Traffic Ratio” or “DNS Queries vs Replies”.
Host overview
I proceed with the biggest circle, the top left one, as the host has around 170 alerts. A mouse over reveals the IP address of 10.12.7.101, clicking on the circle opens the host information page:
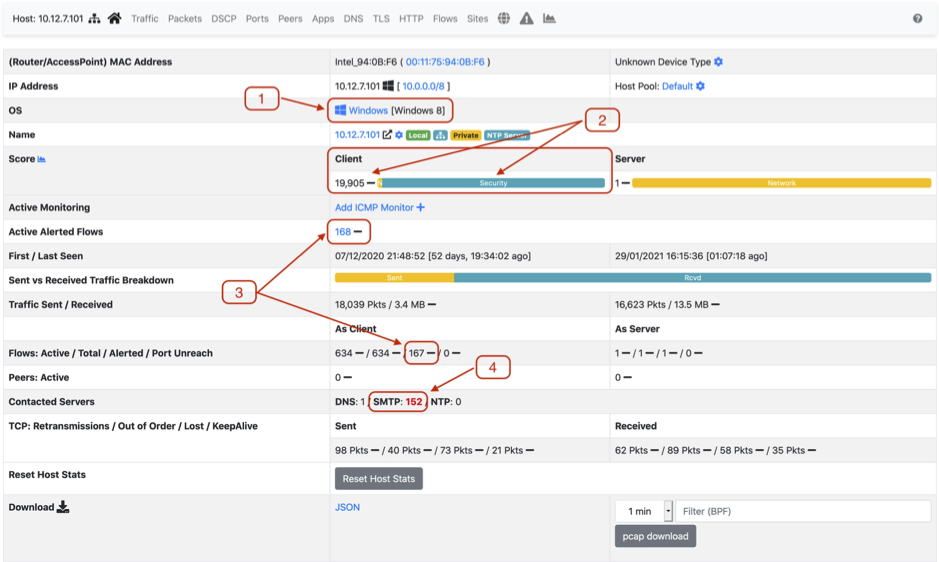
Regarding security concerns, I am interested in the above market items:
- The host is a Windows 8 client
- The host has a security score as a client of 19’905, for a single host a very high number. Ntop uses scores as a risk-based approach to security or protocol related flaws. E.g. malicious data in a flow adds 210 to the host score, suspicious data in a flow adds 200. The idea is not to have absolute values or limits, like above 1000 is bad, below 100 all good, instead, the score can be seen as an indicator of possible problems.
- Out of 634 flows from or to this host, 168 are with an alert. That means that approx. 1/4 of the flows have an issue. Very unusual indeed.
- For this host 152 SMTP (or SMTPS) flows were counted. This means the user is connected to many different SMTP servers. Again, this is very unusual for a client. A average user maybe has 5 or 10 different email accounts, leading to 10+ SMTP flows, but 152 SMTP connections do not look good at all.
Now let us check the alarms generated by ntopng. By clicking on the caution sign , the flow alerts of the host view opens:
Host flow alerts
The list I filter by score, in order to get the alerts with highest score.
Note:
We could further filter the list by “Severity”. But with this host it is not needed, basically there are only Errors, with the highest severity.
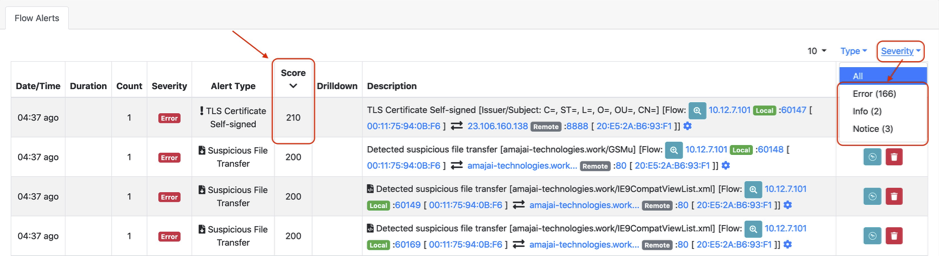
Let us have a closer look at the first error, “TLS Certificate Self-signed”. We can drill down by pressing the Magnifying glass Button:
Flow Details
Here again there is a lot of information about the flow. For the security analysis we take a closer look at the three highlighted items:
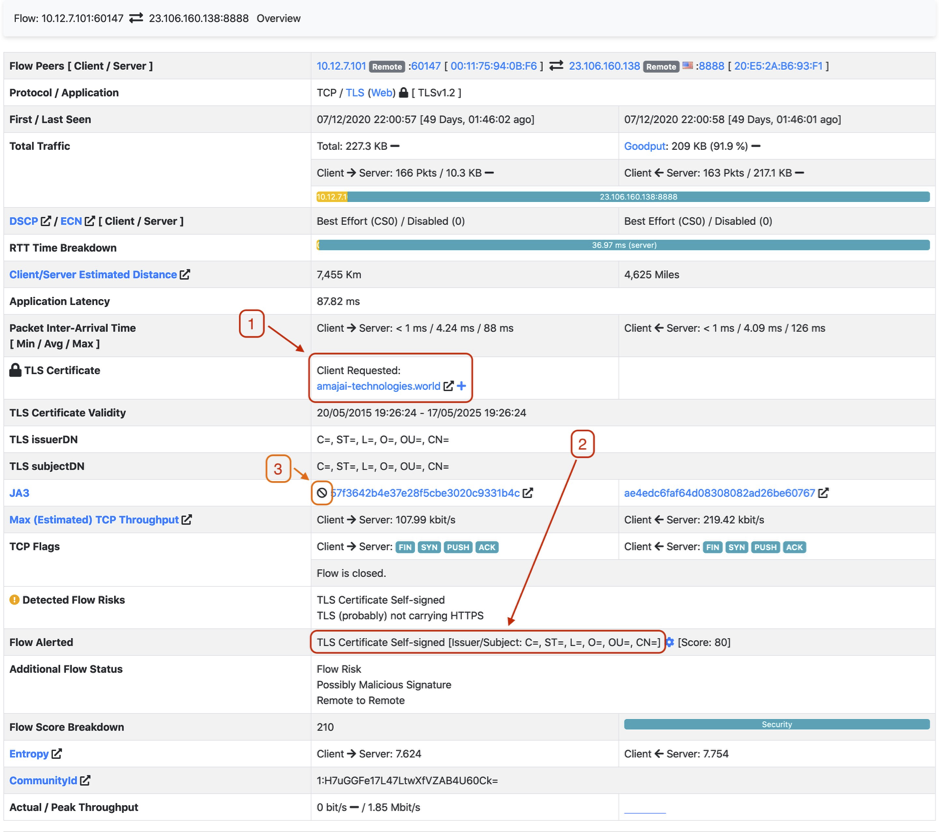
- The extracted url of the client request, hXXp://amajai-technologies[.]world/ looks at first sight accurate, maybe the TLD .world is for a technology provider a bit off. But doesn’t it look similar to what it actually tries to copy, akamaitechnologies.com? Look-alike domains [7] are easily overseen in daily work and are a real cyber security threat.
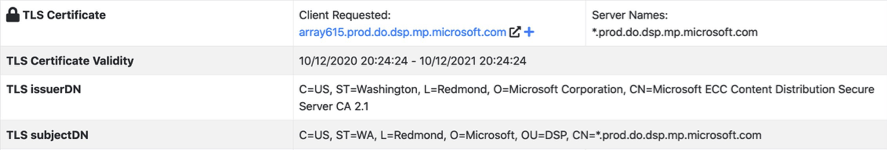
- The TLS certificate is self-signed: Red flag. No reputable or professional service uses a self-signed certificate for external / internet communication. Furthermore the TLS issuer and subject fields are empty, the red flag just got bigger. For reference, how the certificate issuer information looks like:
- Assumptions that something is odd with this flow are validated by the JA3 [8] client fingerprint. The crossed circle, , indicates that the client fingerprint is listed as malicious. Follow the JA3 to sslbl.abuse.ch for further details and yes, the client certificate is malicious:
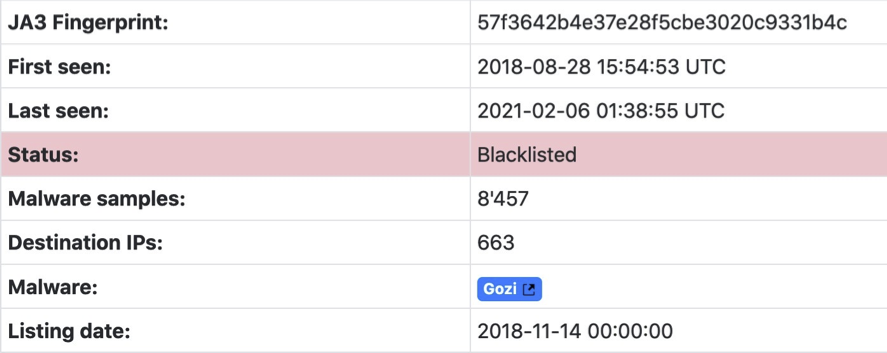
Although the blacklisted JA3 is not Qakbot, we just found out that this host is a well infected with the Gozi banking trojan.
Conclusion
Even for analysing recorded network traffic, ntopng is great help for getting an overview of what happened on the network. But the real value of ntopng is, it does all the scoring and alerting in real time. Facing above malware, I might not know immediately what exact type of malware it is, but the generated alerts are strong indicators that something with that host is not ok and it can be isolated from the network for further analysis.
Got curious? Get started and try to find the spam activity or the Qakbot flow(s) yourself!
We invite other members of our community to contact us if they want to share their work on this blog.
References
- https://www.malware-traffic-analysis.net/2020/12/07/2020-12-07-Qakbot-with-Cobalt-Strike-and-spambot-activity.pcap.zip Note: the zip is password protected. Use infected to extract the pcap.
- https://urlhaus.abuse.ch/browse/tag/Qakbot
- https://malpedia.caad.fkie.fraunhofer.de/details/win.qakbot
- https://www.zdnet.com/article/cobalt-strike-and-metasploit-accounted-for-a-quarter-of-all-malware-c-c-servers-in-2020/
- https://unit42.paloaltonetworks.com/tutorial-qakbot-infection/
- https://packages.ntop.org/
- https://info.phishlabs.com/blog/what-is-a-look-alike-domain
- https://engineering.salesforce.com/tls-fingerprinting-with-ja3-and-ja3s-247362855967
