Mikrotik devices are very popular in the ntop community. The simplest way to monitor traffic of these devices is using flows as described in this blog post. However sometimes flows might not be the best choice for various reasons including the inability to perform DPI on the captured traffic.
For full visibility you can use a different option offered by Mikrotik devices. Under Tools -> Packet Sniffer you can export packets over the TZSP protocol (it is a sort of remote span protocol): just specify the IP of the remote collector and the collector port (usually 37008).
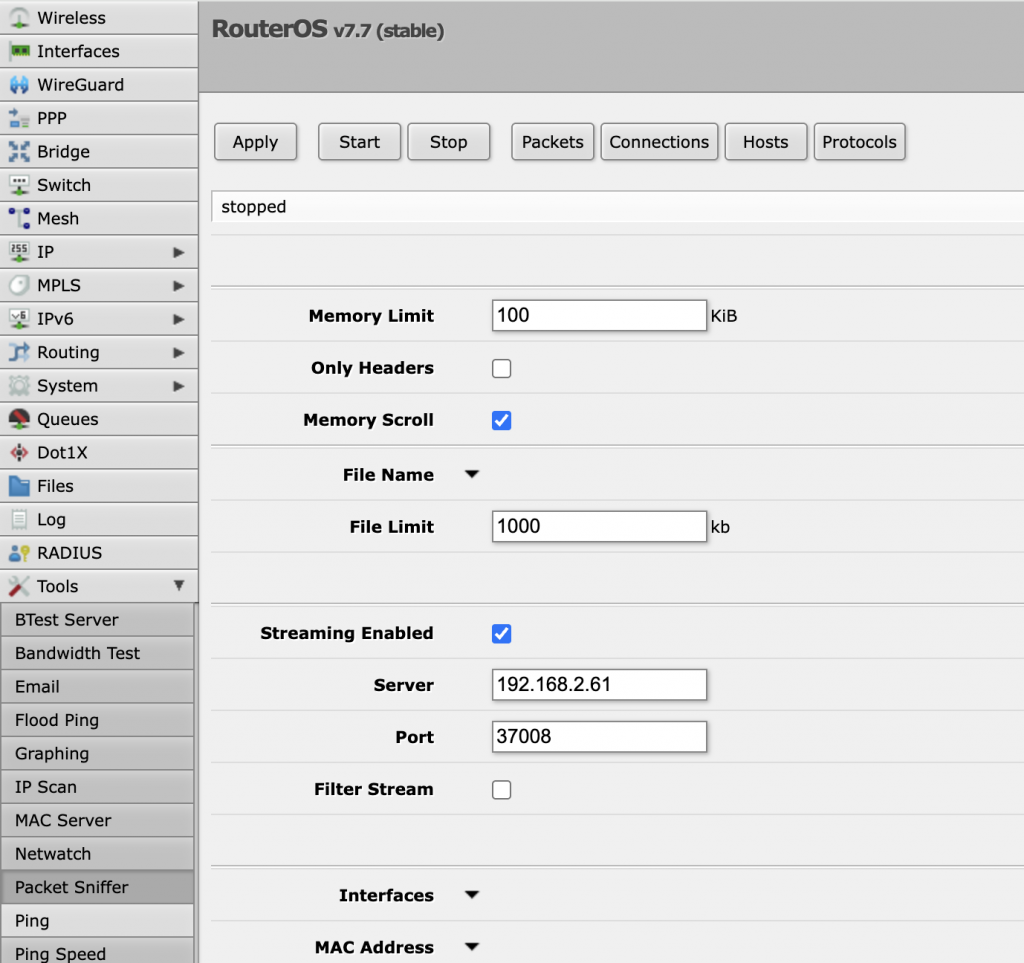
The latest nTap version is able to collect TZSP traffic and transform into something ntop (but also Wireshark and other open source) tools can understand. All you need to do is this:
- [host 192.168.2.61] ntap_remote -t 37008 -c 127.0.0.1:1235 -k hello
- [host 192.168.2.61] sudo ntopng -i ntap:1235:hello
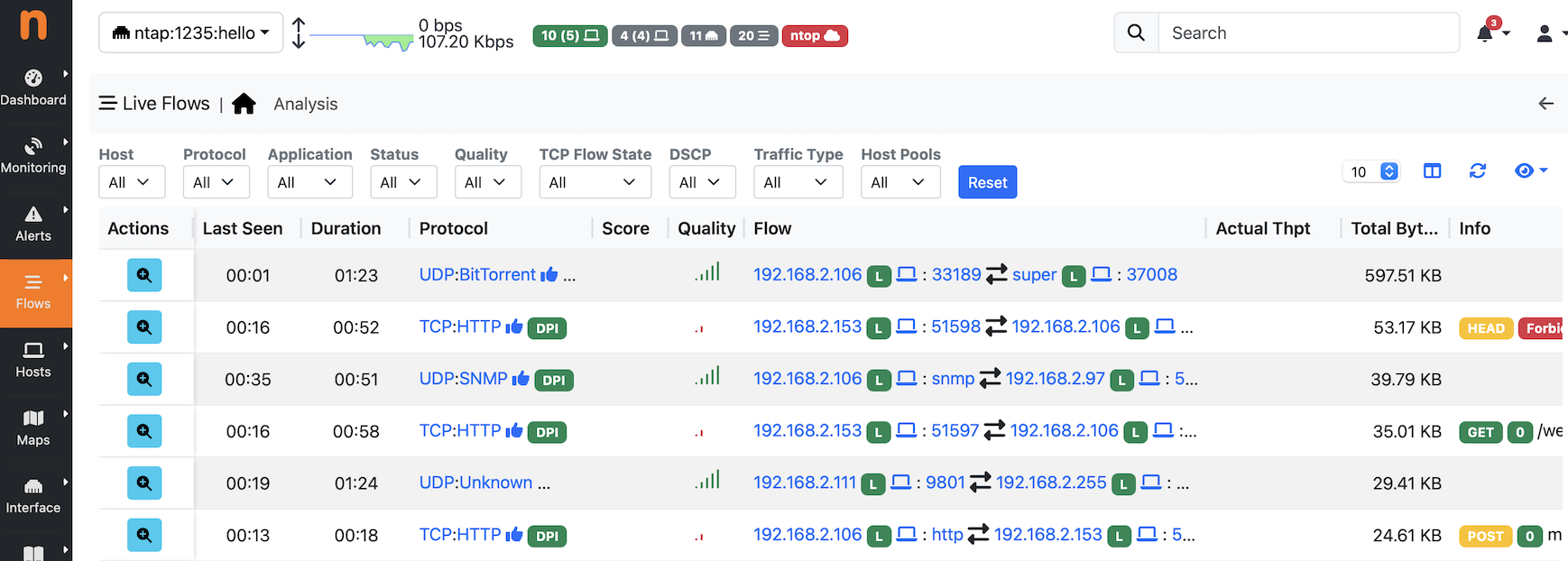
As you can see nDPI is now fully operational contrary to Mikrotik exporting flows where this information is not available,
If you want to use TZSP to export packets from Mikrotik devices, you also have the options to use nProbe to collect TZSP packets and transform them into flows. You can achieve this as follows:
- [host 192.168.2.61] nprobe -3 37008 –zmq tcp://127.0.0.1:1235
- [host 192.168.2.61] sudo ntopng -i tcp://127.0.0.1:1235
Enjoy !
