ntopng has several ways to spot unusual traffic patterns, like:
- Checking if a device is behaving strangely.
- Sending alerts when a threshold is reached.
- Looking for changes in traffic metrics (like how much traffic is coming from a particular host).
- Seeing if host services change.
To make these checks even better, ntopng added a new flow behavioral check called “Host Policy.” The idea is simple: there are some special devices on a network, like routers, switches, printers, and other non-general-purpose devices, that shouldn’t send traffic to the Internet. Except for a few specific sites or hosts that they usually contact for things like checking new software or setting the clock.
To use the “Host Policy” check, go to the menu Policies -> Network Configuration. Under the Policies menu, you can set network configuration options that are only available when the check is enabled.
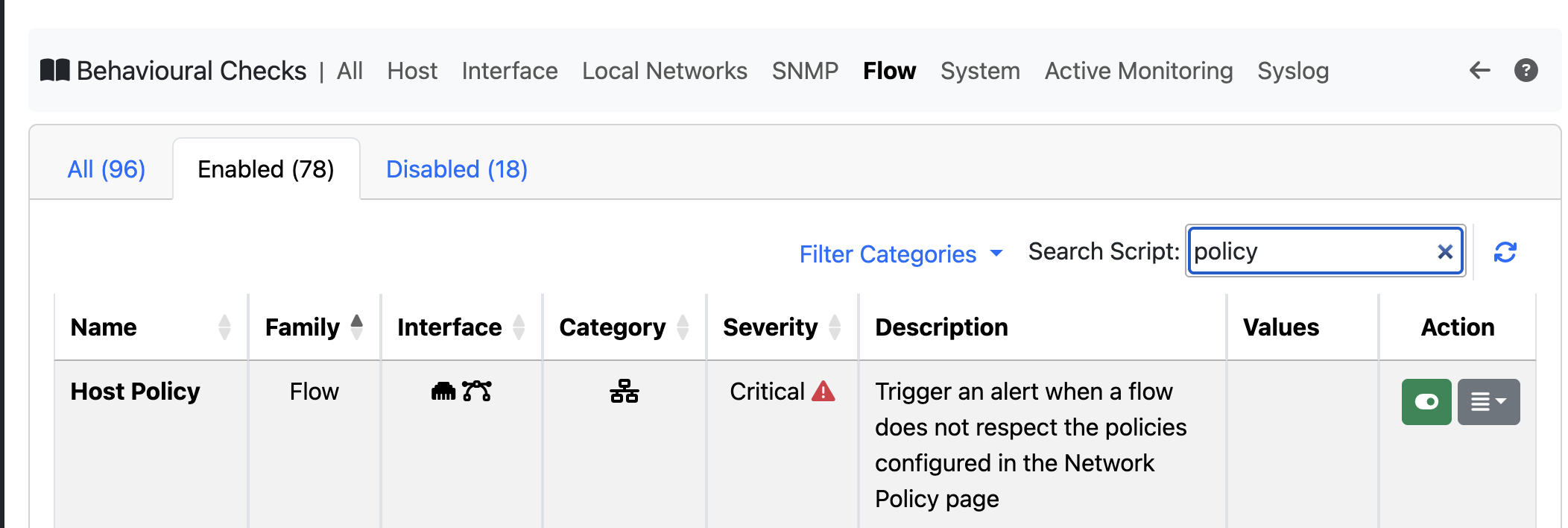
Done that, it is possible to specify the network configuration policy page.
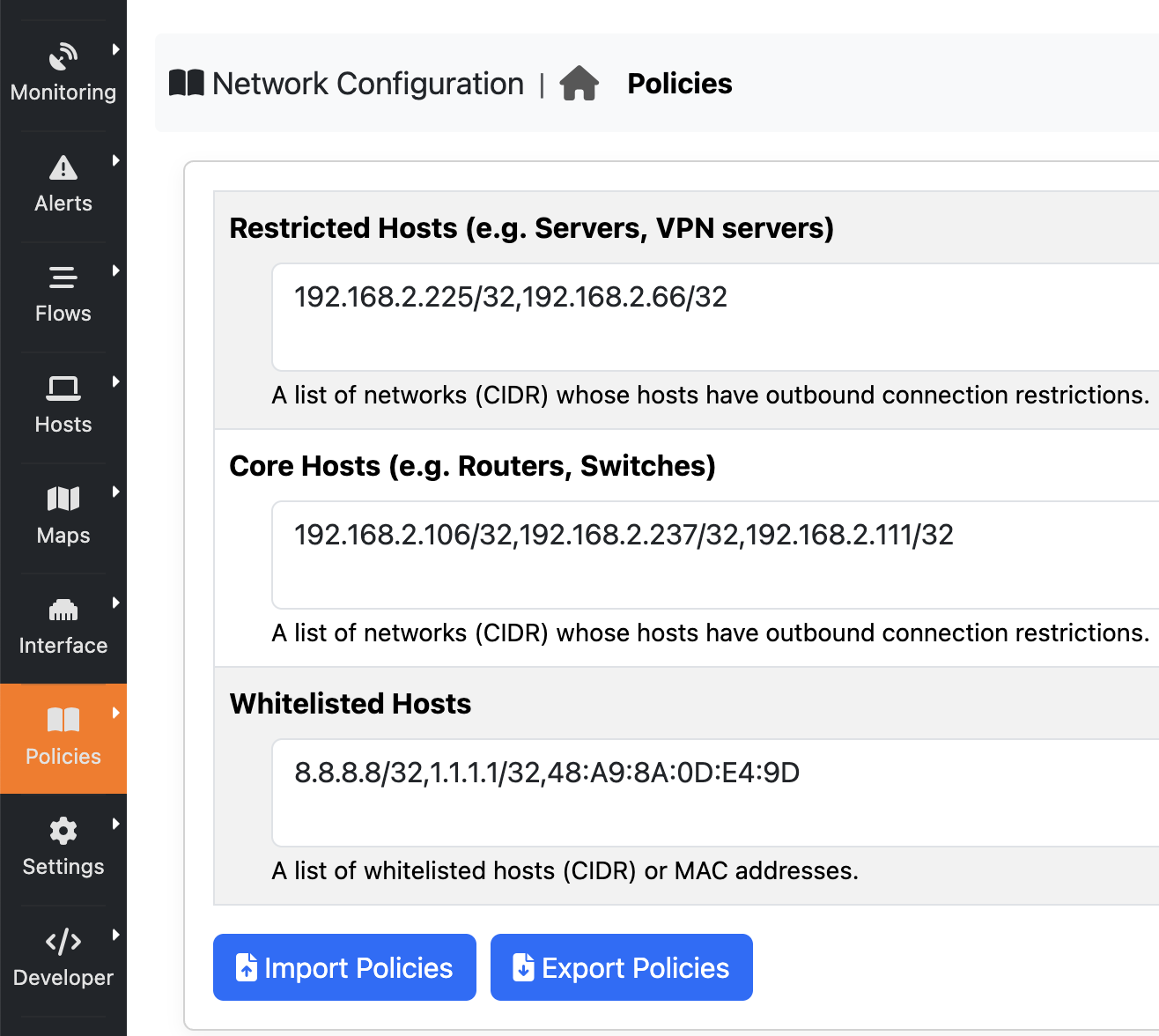
The page has three sections:
- Restricted hosts are devices that offer services (like a VPN or database server) that other hosts use. They’re not supposed to send any traffic, except to the list of whitelisted hosts.
- Core hosts are usually devices like routers, switches, or printers that provide network-wide services that other hosts can access. But they’re supposed to be “silent,” meaning they don’t send any connections. The difference between restricted and core hosts is that restricted hosts have the same restrictions as core hosts, plus they can’t connect to core hosts. For example, if a database server tries to connect to a router using SSH, that means the host is acting up because core hosts are special hosts that only network administrators can access.
- Whitelisted hosts are a list of IP or MAC addresses that both restricted and core hosts can connect to.
An alert is triggered if:
- A restricted host tries to connect to a public IP address that’s not on the whitelist.
- A restricted host tries to connect to a core host.
- A core host tries to connect to any address that’s not on the whitelist.
Here’s how you can use this simple mechanism to detect some important things:
- If restricted or core hosts try to connect to hosts that aren’t supposed to be contacted, it’s a big red flag. For these hosts, the policy is set to “deny all” except for the whitelisted hosts.
- If a core network device like a switch starts a connection, it’s a sign that something’s gone wrong. It’s supposed to be an active network component, so this is a serious issue.
Right now, you’ll need to manually configure the above page, but we’re working on a future release that will let ntopng suggest a possible configuration.
Enjoy!
