nEdge
Protects all of your digital assets and online activities
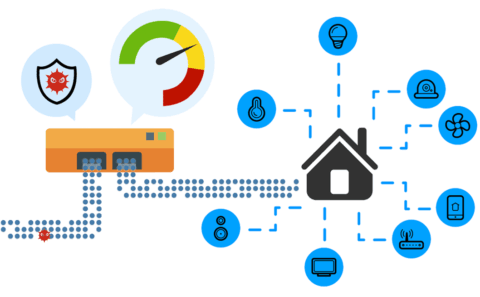
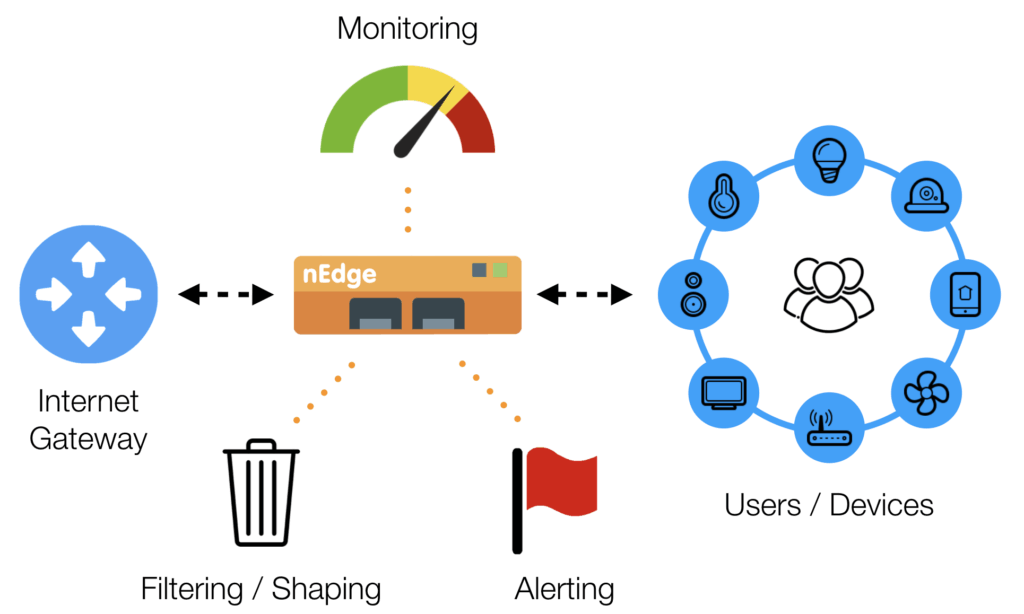
nEdge, also known as ntopng Edge, is a software application designed to solve a few problems:
- Bind devices to users
- Specify per-user layer-7 protocol policies (e.g. use X can use protocol Y)
- Protect the network from malware and connections from/to unsafe destinations.
- Make sure that the available Internet bandwidth is shared evenly by preventing bandwidth hogs.
Make the Network A Safe Place Again
nEdge ensures the Internet is always available for business-critical applications by preventing misbehaving hosts from jeopardizing the bandwidth. nEdge also secures the network against unwanted traffic such as torrents or cloud uploads that can pave the way for data breaches.
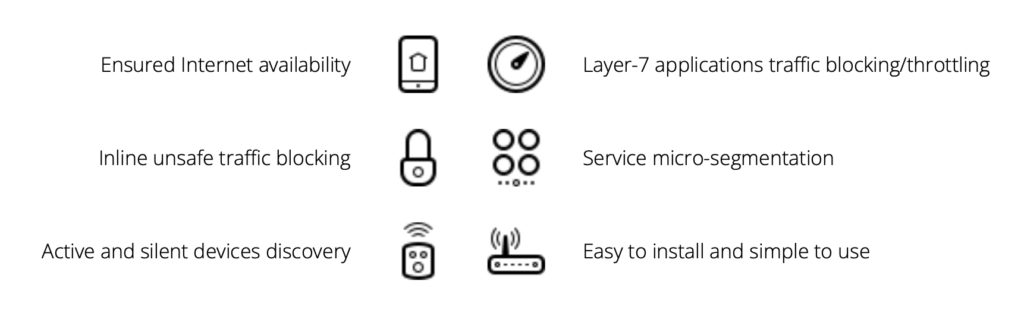
Ensured Internet availability
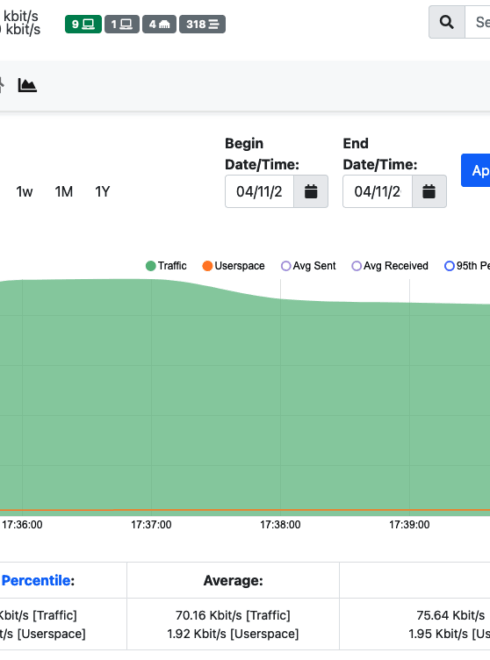
nEdge helps network administrators ensure a smooth, controlled operation of complex networks by accurately managing the many different connected devices that compete to access the Internet. Internet access is almost always limited by download and upload bandwidths provided by the Internet Service Provider (ISP) and such bandwidths get easily saturated, especially when many multiple devices are accessing the Internet. It is common to experience a “bad Internet” in crowded public Internet places, including hotels, cruise ships, bars and restaurants where even just a single device has the potential to jeopardize the network and negatively affect the Quality of Experience (QoE) of all the other devices.
nEdge provides an intuitive Web-Based graphical interface to control how the available Internet bandwidth is used among the devices. The maximum download and upload bandwidths can easily be policed for any device with just a handful of clicks. Similarly, a policy for the minimum guaranteed upload and download speeds can be set for every device.
Examples of bandwidth controls supported include:
- “Share the available upload and download speed evenly among all the connected devices”
- “Reserve at least 50% of the download bandwidth to important devices”
- “Share the 70% of the available bandwidth evenly among customers, and the other 30% evenly among the staff”
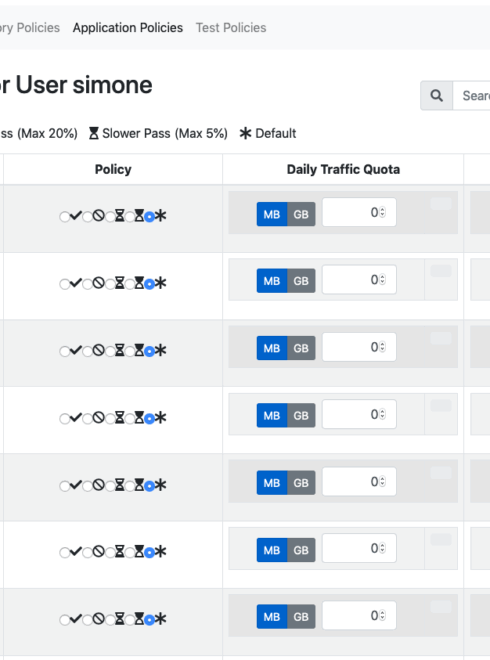
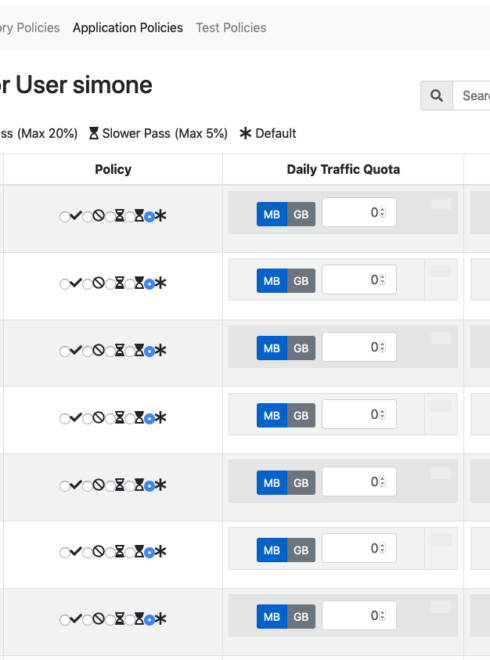
nEdge allows even a finer bandwidth control which takes into account also human users (rather that just devices) and Layer-7 application protocols. Layer-7 policies can quickly be set for example to prevent Tor from being used or to throttle BitTorrent, just to name a few.
Layer-7 applications traffic blocking/throttling

It is often hard to protect networks from unwanted applications traffic. In addition, internal rules (e.g., company ethics and conduct rules) and external regulations may impose limits on the allowed websites as well as on the Layer-7 applications traffic permitted. Are you fed up with people using cloud services or with those that are downloading copyrighted contents Are your employees spending to much time visiting recreational sites during normal office hours? nEdge can enforce policies to block or throttle Layer-7 applications traffic without requiring changes in the network topology that can be expensive and create conflicts with pre-existing equipments and configurations.
nEdge performs Deep Packet Inspection using the home-grown nDPI library to first detect and then block or throttle Layer-7 application protocols. Layer-7 policies can quickly be set for example to prevent unwanted applications from being used by certain devices.
Examples of Layer-7 policies that can be set are:
- “Block BitTorrent and Tor traffic generated from company’s workstations”
- “Throttle media streaming to at most 10% of the available download bandwidth”
- “Only allow printers to perform IPP and block any other kind of traffic they could try to generate”
This kind of policies is very powerful even when it comes to security. Think to IoT devices, for example. Such devices are very often shipped with old, outdated firmwares and they rarely receive security updates. Hence, they have the potential to open security breaches in your network. Being able to enforce a set of secure, permitted Layer-7 applications will ‘wrap’ insecure IoT devices in a secure, protected environment that stays ahead of threats.
However, being able to set policies on certain devices is just a part of the story. As humans often like to think less in terms of devices and more in terms of other humans when it comes to control who is accessing the internet, nEdge allows to enforce policies on Internet “users”. No matter if Simone is using his iPad, his iPhone, or his Xbox. Simone is just a human that is accessing the Internet and nEdge allows to enforce policies for Simone, policies that are transparently applied to all his devices as if they were a single one.
Policies on Internet “users” that can be enforced with nEdge include:
- “Don’t let the kids Maria and Nate play online games now that is dinner time”
- “Only allow John to perform Apple updates at night”
Inline unsafe traffic blocking
nEdge actively inspects all the network traffic and make sure no one can reach, or be reached by, an unsafe host. Its technology leverages IP and domains lists produced and constantly updated by Industry’s leading cyber-security companies to assure not even a single byte is exchanged with potentially harmful hosts. Currently supported lists are those provided by Malware Domain List and Emerging Threats and are refreshed every day.
nEdge integrates safe DNS with IP and domain lists to provide continuous protection. If someone is trying to contact a malicious host or if a malicious host is trying to reach someone on your network. nEdge will automatically generate an alert and block communications involving a malicious peer. And if you want to be real-time informed on ongoing threats, simply configure the Slack integration to receive alerts on the smartphone!
nEdge can seamlessly and transparently enforce the use of safe DNS servers. Every DNS request seen is forcefully routed to make sure it is handled by a trusted, safe DNS to protect you against the most common cyber threats. Several DNS servers provided by cyber-security companies are ready to be chosen and can be used free of charge within nEdge. And if you are concerned about someone who could try to manually force an arbitrary DNS, don’t worry! nEdge sees and routes every DNS request to the safe DNS. Additional protection is also offered for kids with special Child-Safe DNS, to protect them against violent or explicit material.
Service micro-segmentation
With service micro-segmentation, administrators create policies that explicitly permit only certain traffic to be exchanged. Policies, security settings are tailored individually on an host basis, depending on the role and function of each host. In this zero-trust security model, nEdge allows you to set up policies. For example, it can force IoT sensors to only talk MQTT, or Web servers to only talk HTTP/HTTPS with clients and MySQL with backend database servers.
nEdge lets you do a very accurate micro-segmentation to safely isolate critical hosts and services from unwanted or unexpected traffic. Traditional firewalls, intrusion prevention systems (IPS) and other security systems are designed to inspect and secure traffic coming from the Internet, but they fail at limiting potentially harmful activities coming from the inside of the network, for example when hackers gain access through a security breach. nEdge micro-segmentation gives greater control and protection over such kind of activities, allowing only certain kinds of traffic to be exchanged with any controlled host. The ultimate goal is to reduce the network attack surface: by applying segmentation rules down to the single host, the risk of insider threats is greatly reduced.
Typical policies that allows you to obtain micro-segmentation with nEdge are:
- “Only allow a Web server to talk HTTP/HTTPS traffic with clients, and MySQL with backend database servers”
- “Only allow switches to talk SNMP and sFlow with a given collector”
- “Only allow a POS to communicate via HTTPS with the Bank website”
Active and silent devices discovery
nEdge discovers and accurately categories all the devices connected to the network, including those that are silent. Discovery and identification produce a rich set of information that include the device type, family, and (when possible) the model and the operating system for a wire range of devices. nEdge also detects new network connected devices, as well it can send alerts when unknown devices. Learn more in this post.

How Does It Work?
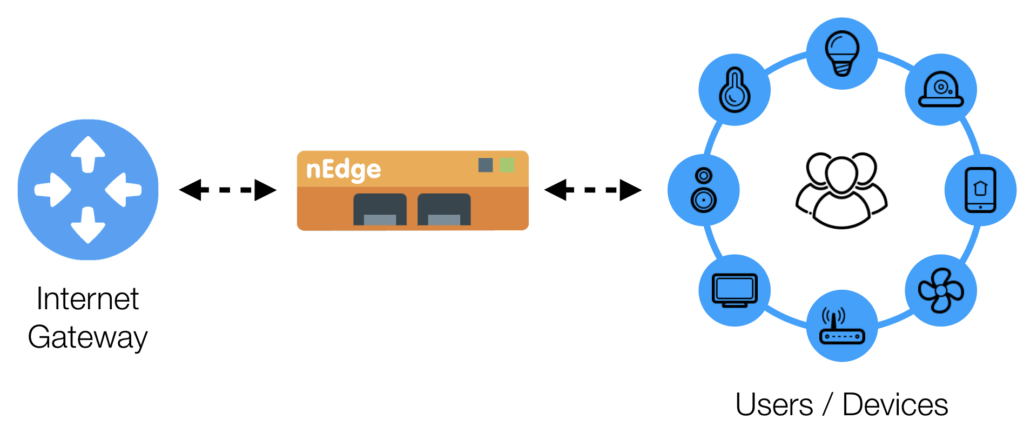
nEdge expects to protect a Local Area Network (LAN), so called edge. Typically, clients and digital assets that require protection reside in the LAN and must go through the WAN to browse the Internet.
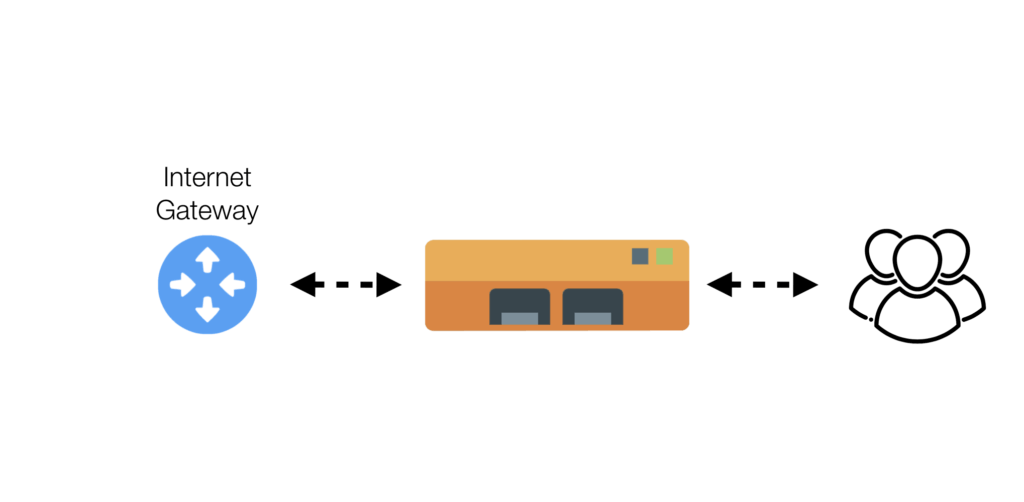
Bridge
nEdge creates a transparent bridge between two network interfaces, one connected to a LAN and the other to a WAN. nEdge operates over the bridge where configured network policies are enforced.
This is the right mode for you if you need a quick and transparent way to secure LAN-to-WAN communications without reconfiguring any devices or IP address.
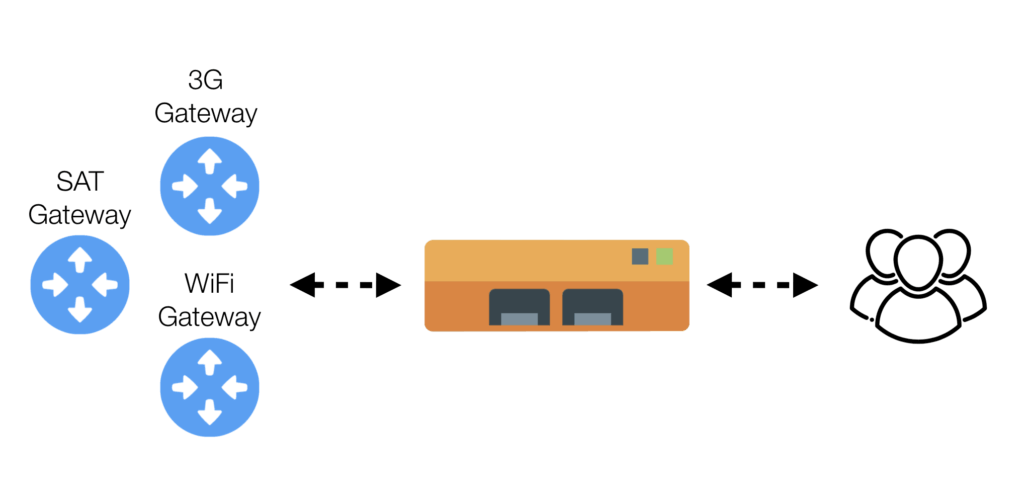
Router
nEdge routes the traffic and decides which traffic should be routed and which traffic should be discarded. Multiple WAN interfaces are supported to allow also decisions on which WAN interface should be used for the routing.
This is the right mode for you if you want to create a (single-LAN or multi-WAN) router that routes traffic on a per-device basis as well as on Layer-7 applications.
at a glance
Key Features
- Layer-7 applications traffic blocking/throttling: enforce policies on the basis of Layer-7 applications traffic and define per-user and per-Layer-7 application time and traffic quotas
- Ensured Internet availability: enforce the maximum download/upload bandwidth, guarantee the minimum download/upload bandwidth
- Inline unsafe traffic blocking: use industry’s leading cyber-security companies IP and domains lists, enable the use of Child-Safe DNS, secure DNS to block malicious domains
- Captive portal: authenticate users with a login page before allowing them to access the Internet. Authentication facilitates the association between a user and his/her devices, and the consequent enforcement of configured policies
- Bridge mode: create a bridge between two network interfaces, one connected to a LAN and the other to a WAN
- Router Mode: route the traffic coming from an interface connected to a LAN towards one or more WAN interfaces, define routing policies to be applied on a per-user basis (e.g., premium users via SAT and basic users via WiFi)
- Load balancing and failover: in router mode, when multiple WANs are configured, powerful routing policies can be implemented on a per-user basis
- Failover: constantly monitor Internet reachability and automatically exclude gateways that can no longer access the Internet
Ideal for Every Environment
Use Cases
SMEs
Small and Medium Enterprises (SMEs) often struggle to protect their networks from unwanted Layer-7 application protocols. Internal rules (e.g., company ethics and conduct rules) or external regulations (e.g., GDPR) may impose limits on the websites visited as well as on the Layer-7 application protocols used in the network. For example, cloud storage may not be allowed to prevent employees from uploading sensitive data to the cloud. Similarly, access to recreational sites such as FaceBook and YouTube may be limited or not allowed during normal office hours.
nEdge can enforce such kinds of rules and regulations without requiring changes in the network topology that can be expensive and create conflicts with pre-existing equipments and configurations. nEdge can also generate alerts when a new device connects to the network, and block possibly dangerous protocols like file sharing protocols, SSL traffic with no certificate and VPN tunnels.
Internet Access Providers
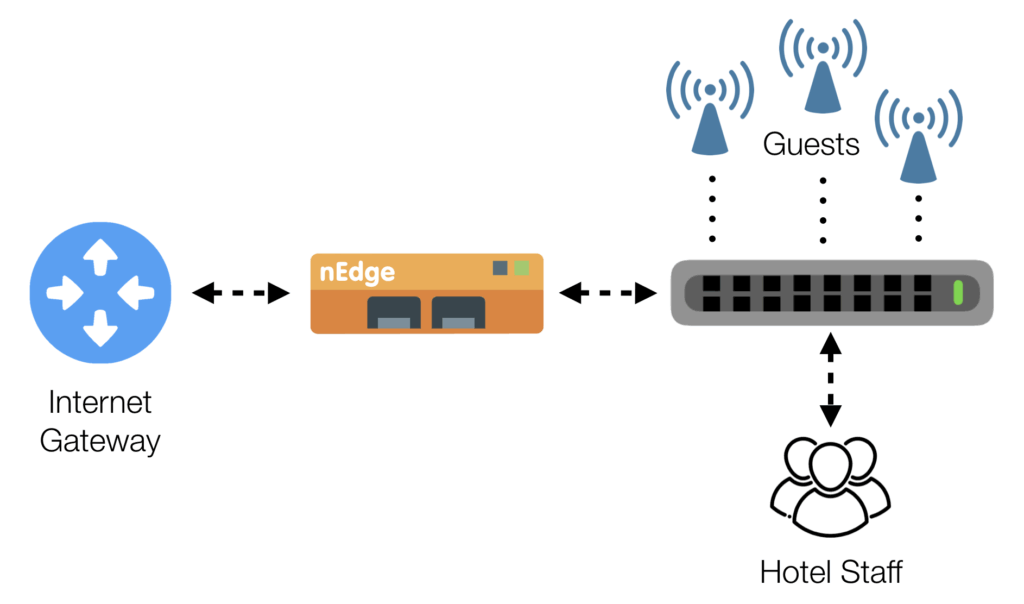
Hotels, bars and restaurants, malls, and more in general public places, almost always provide complimentary or paid internet access. Hotels offer Internet access to their guests. Similarly, bars and restaurants provide Internet access to their customers. However, it is common for those providers to have a single Internet gateway, which is usually the same as the one being used by the hotel staff. Under these circumstances, a misbehaving client, or just a large number of connected devices, can easily jeopardize the Internet access and undermine normal business operations. Today, critical operations such as Point-Of-Sale (POS) payments, reservations, and accounting must be performed online and a broken Internet access almost immediately translate into a loss of money.
nEdge helps in protecting business-critical operations by automatically identifying normal guests and staff people and devices, and prioritizing their traffic according to different policies. So for example on can guarantee a minimum bandwidth to the staff, and allow guests to run at full bandwidth only when when the staff is idle. Moreover, guests’ bandwidth can be evenly divided among all the active guests, so that a single user won’t be able to jeopardize the Internet access. For further control, some bandwidth-consuming protocols like BitTorrent can also be disabled or throttled down to a very small portion of the total available bandwidth.
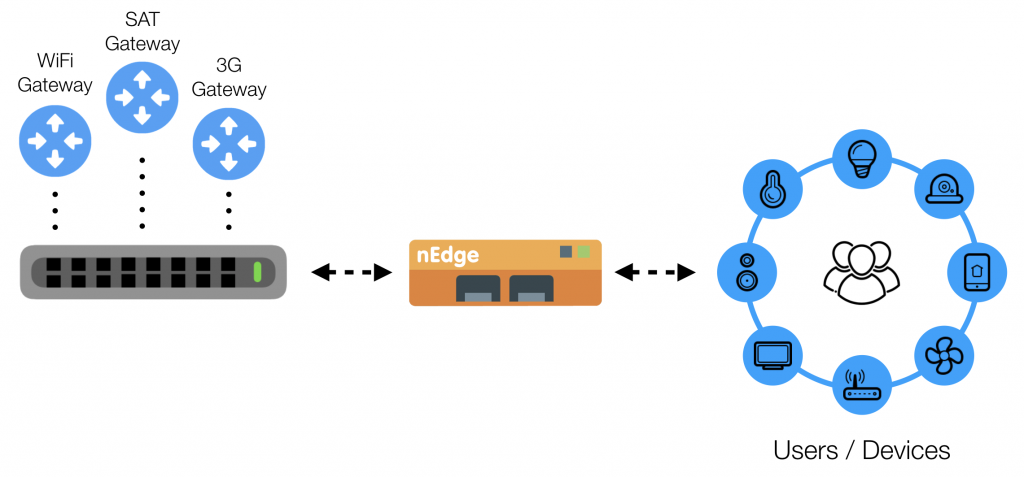
Multi-WAN / Multi-Homed Providers
nEdge includes advanced functionalities specifically designed for private Internet access providers, characterized by the presence of a number of Internet gateways with different speeds and costs (e.g. WiFi, 3G, SAT). In these environments there are often different users plans, for example:
- Basic User: can only use WiFi, with a rate limit.
- Normal User: can use WiFi by default, but are also allowed to use 3G if WiFi is not available.
- Gold User: can use any of the available gateways, with bandwidth reserved.
Users should always use the less expensive gateway available, based on their plan. If such a gateway becomes unavailable, users should use an alternative gateway, according to gateways priority and users plans, and switch back to the less expensive gateway when available.
nEdge can manage manage scenarios such as those described above. It is just a matter of configuring multiple gateways with priority and routing policies based on the users plans. nEdge also takes care of failover and load balancing, monitoring the gateways status and switching to higher priority gateways (less expensive or more performant) when available.
Specifications
Tech Specs
- Ubuntu Linux 20/24 LTS
- Web GUI available through any HTML5-ready browser
- HTTP-based RESTful API
- TLS/HTTPS support
- Lua scriptability
- Ethernet/VLAN
- IPv4/IPv6
- TCP/UDP/ICMP
- 450+ Layer-7 application protocols supported by nDPI
models
Choose Your Model
Did you already install the software?
Select the model. Different models unlock different features and capacity. Check the comparison table.