JA4 is a modern network fingerprinting standard used to identify and profile clients initiating encrypted TLS (Transport Layer Security) connections. JA4 it is the successor to the widely used but now deprecated JA3 standard.
JA3 is considered obsolete because it cannot provide a stable identifier for modern browsers and is easily bypassed by attackers. Its reliance on the specific sequence of fields in the TLS ClientHello message makes it highly fragile in today’s networking environment. One (but not the only one) of the main limitations is JA3 is sensitivity to ordering: JA3 generates a hash based on the exact order of TLS extensions and cipher suites. Below you can see a Wireshark packet capture of a macOS workstation that connects to this website using Apple Safari (version 26.2).
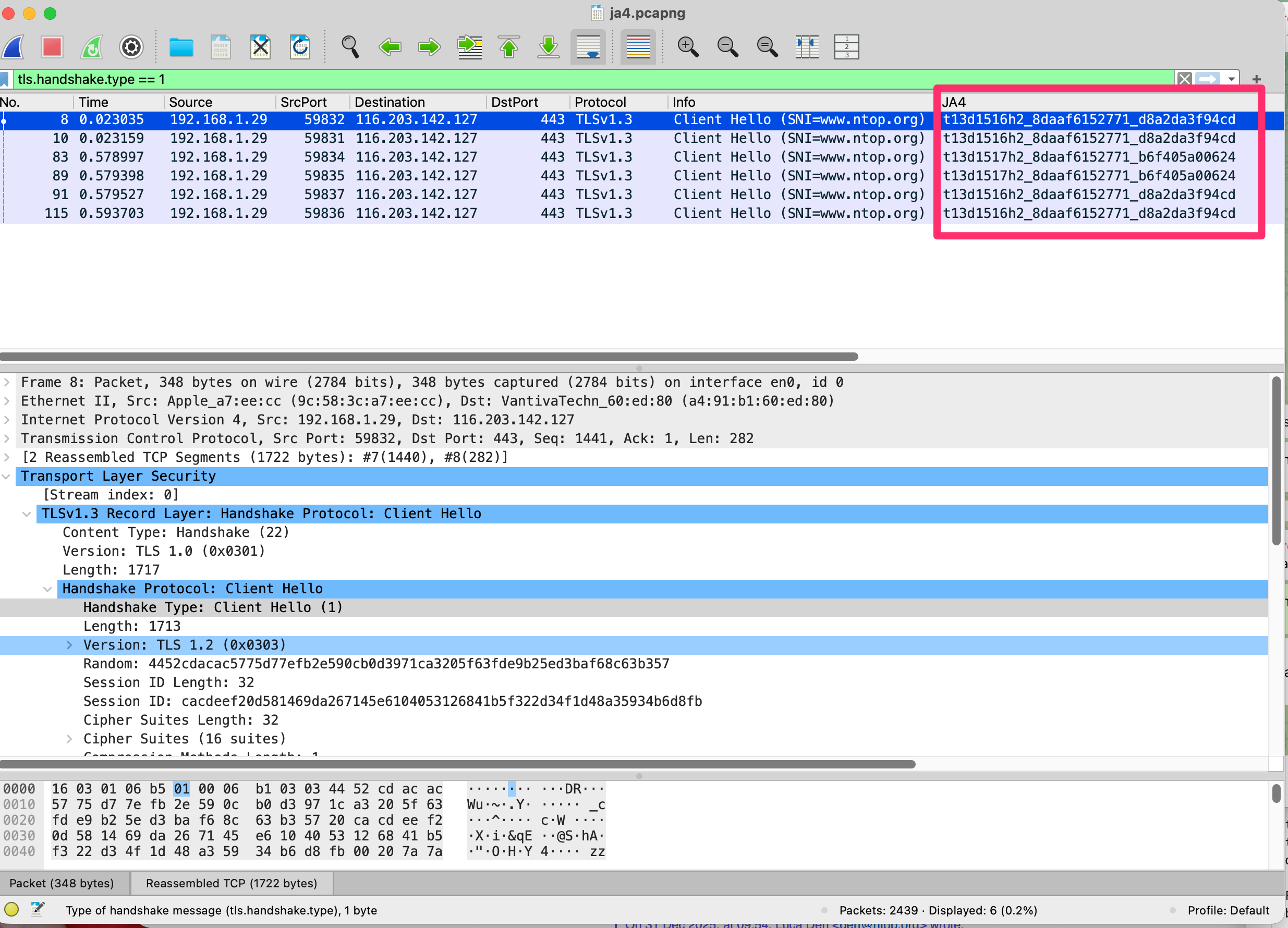
As you can see all the requests are issued by the same browser/IP but the JA4 signature is not unique. This is unexpected as JA4 in this case is expected to be the same across all the requests, violating one of the core properties of JA4 fingerprint.
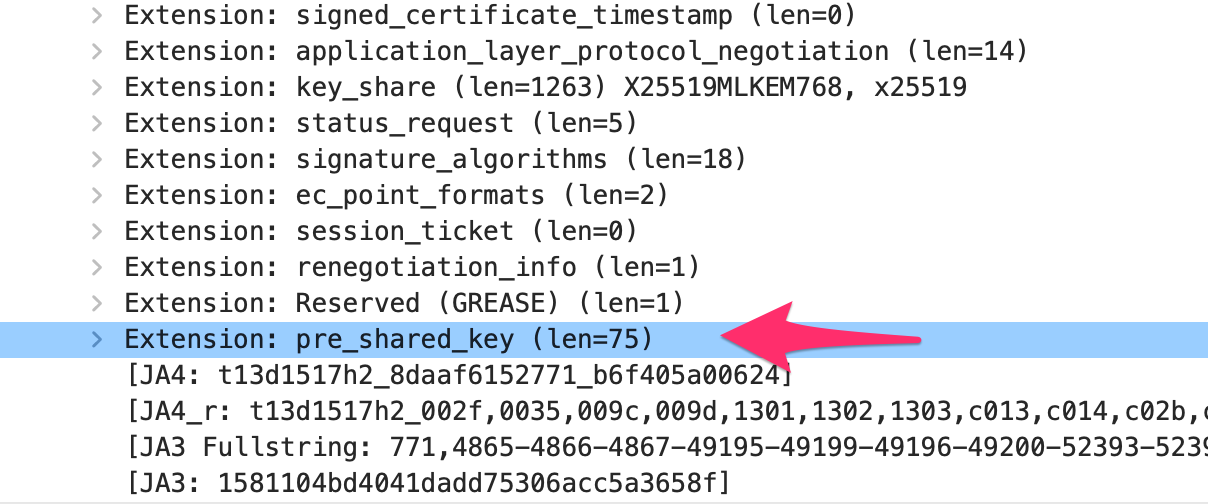
Analyzing the request we noticed that Safari uses the pre-shared key TLS extension (RFC 8446) to use the PSKs of a previously established connection to establish a new connection. This explains why JA4 is not unique, but it also shows a limitation of JA4 that also obsoleted JA3.
Until a JA5 standard is published, in nDPI we have introduced a new option that allows “ephemeral” TLS extensions not be to accounted in JA4 computation. For compatibility reason this new feature is disabled, but it can be enabled at command line as follows. This is the standard JA4
/ndpiReader -i ~/Downloads/ja4.pcapng -K json -k out.json -q ; cat out.json | jq | grep ja4
"ja4": "t13d1516h2_8daaf6152771_d8a2da3f94cd",
"ja4": "t13d1516h2_8daaf6152771_d8a2da3f94cd",
"ja4": "t13d1517h2_8daaf6152771_b6f405a00624",
"ja4": "t13d1517h2_8daaf6152771_b6f405a00624",
"ja4": "t13d1516h2_8daaf6152771_d8a2da3f94cd",
"ja4": "t13d1516h2_8daaf6152771_d8a2da3f94cd",and this is the new fingerprint where ephemeral extensions are ignored
ndpiReader --cfg "tls,metadata.ja_ignore_ephemeral_tls_extn,1" -i ~/Downloads/ja4.pcapng -K json -k out.json -q ; cat out.json | jq | grep ja4
"ja4": "t13d1515h2_8daaf6152771_31ec0a762479",
"ja4": "t13d1515h2_8daaf6152771_31ec0a762479",
"ja4": "t13d1515h2_8daaf6152771_31ec0a762479",
"ja4": "t13d1515h2_8daaf6152771_31ec0a762479",
"ja4": "t13d1515h2_8daaf6152771_31ec0a762479",
"ja4": "t13d1515h2_8daaf6152771_31ec0a762479",As you can see they are all alike, and JA4 is now useful again.
As of today ephemeral TLS extensions include
New extensions can be added as they appear. Enjoy JA4 again !
