In the past couple of years we have added the concept of flow risk in nDPI that allows issues with flows to be detected (for instance expired TLS certificates). Unfortunately we need to silence some of these risk exceptions as some hosts/domain names produce risks that need to be ignored (for instance an outdated device that cannot be replaced and that has been properly protected by the security policies). In ntopng you can disable them clicking on the flow alert that will open a window as the one below,

and review exclusions from the settings menu:
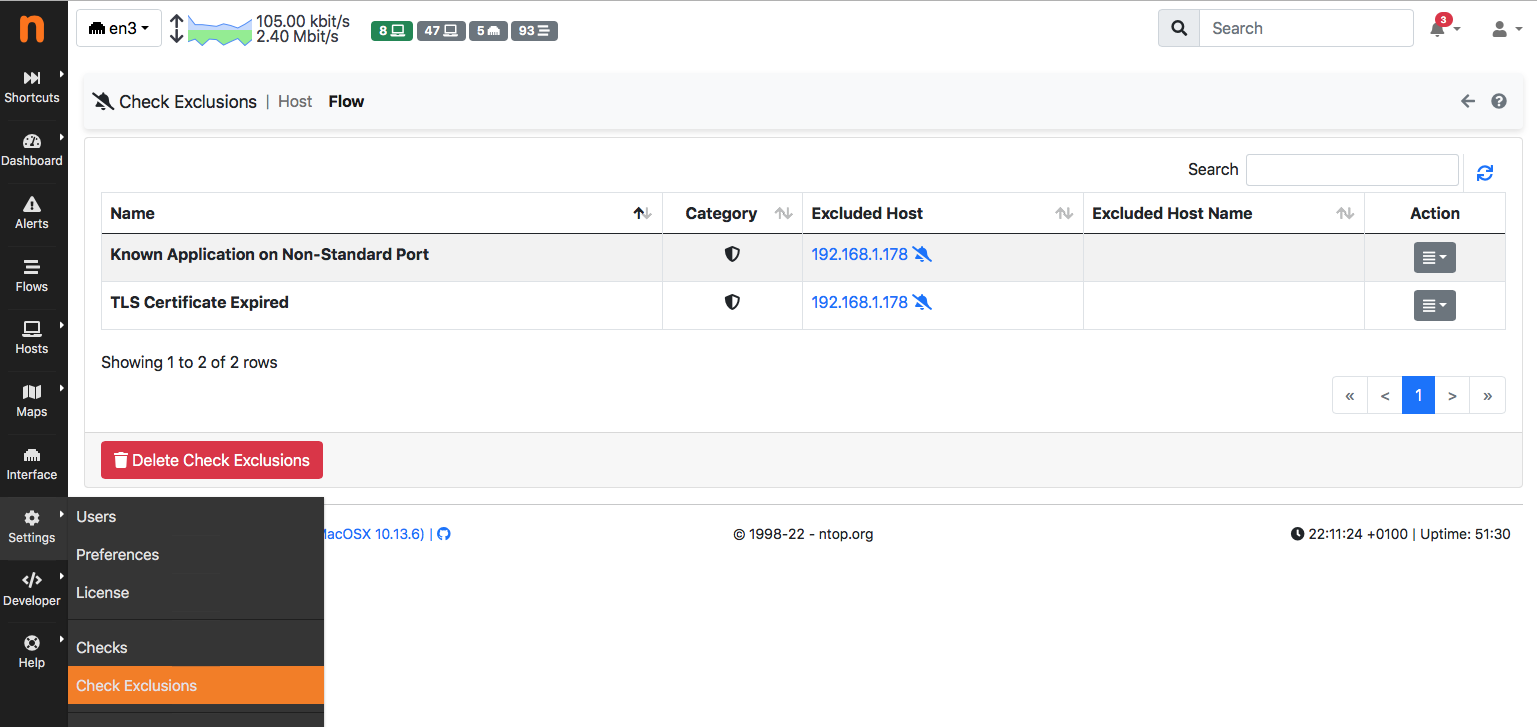
This feature is useful when a few exceptions need to be silenced, but it is limited when you want to set more exceptions based on domain names or networks (CIDR). Not to mention that other nDPI-based tools such as nProbe don’t feature this mechanism.
In order to address this need, you can specify a nDPI protocol file that contains exceptions as follows:
# # Risk Exceptions # # ip_risk_mask: used to mask flow risks for IP addresses # host_risk_mask: used to mask exceptions for domain names and hosts # # Syntax: <name>=<64 bit mask to be put in AND with the risk # # For IPs, the flow risk is put in AND (source IP mask OR destination IP mask) # For Flows with a hostname (e.g. TLS) the risk is also put in AND with the host_risk_mask ip_risk_mask:192.168.1.0/24=0 ip_risk_mask:10.196.157.228=0 host_risk_mask:".local"=0 host_risk_mask:".msftconnecttest.com"=0
where you can specify a list of networks and domain names for which risks can be masked. A 0 mask means all risks are masked, whereas you can specify a bitmap for masking specific risks. Here you can find the list of known risks so if you want to mask for CIDR 192.168.1.0/24 the risk TLS Certificate Mismatch (id 10), you need to create a 64 bit mask with bit 10 set to zero and all bits set to 1 (i.e. 0xFFFFFFFFFFFFFDFF in hex).
You can pass this protocol file to ntopng as
[--ndpi-protocols|-p] <file>.protos | Specify a nDPI protocol file
| (eg. protos.txt)
and as
--ndpi-custom-protos <path> | Custom nDPI protocols path.
in nProbe.
In addition to this, it is also possible to specify trusted CA certification authorities, often used to issue TLS certificates used in company networks. This can be defined in the protocols file as follows:
# Custom certification autorities we trust trusted_issuer_dn:"CN=813845657003339838, O=Code42, OU=TEST, ST=MN, C=US"
so that nDPI will not generate TLS Certificate self-signed for the above CA.
Enjoy !
