A category list is a control mechanism used to label traffic according to a category. In nDPI, the traffic classification engine on top of which ntop applications are built, there are various categories including (but not limited to)
- mining
- malware
- advertisement
- file sharing
- video streaming
A blacklist is a list of IP addresses or symbolic domain names, that is used to label malicious traffic. These lists are often computed using honeypots, that in essence are hosts or services deployed on a network (usually the Internet) that are easy to break-in and that when used/attacked they act as a modern litmus paper for spotting attackers and intruders.
Blacklists usually contain public IP addresses/domain names as they are used to “anticipate problems”: this because if an IP address has been put on a blacklist, such host did something bad so some hosts on the Internet, and thus when we see traffic for such host, we need to be careful as probably we’re under attack/scan. Please note that blacklists and honeypots can also be deployed on private networks: for instance you can keep a range of unassigned IP addresses in your network and add them to a blacklist, to spot internal hosts that are scanning your LAN via lateral movements.
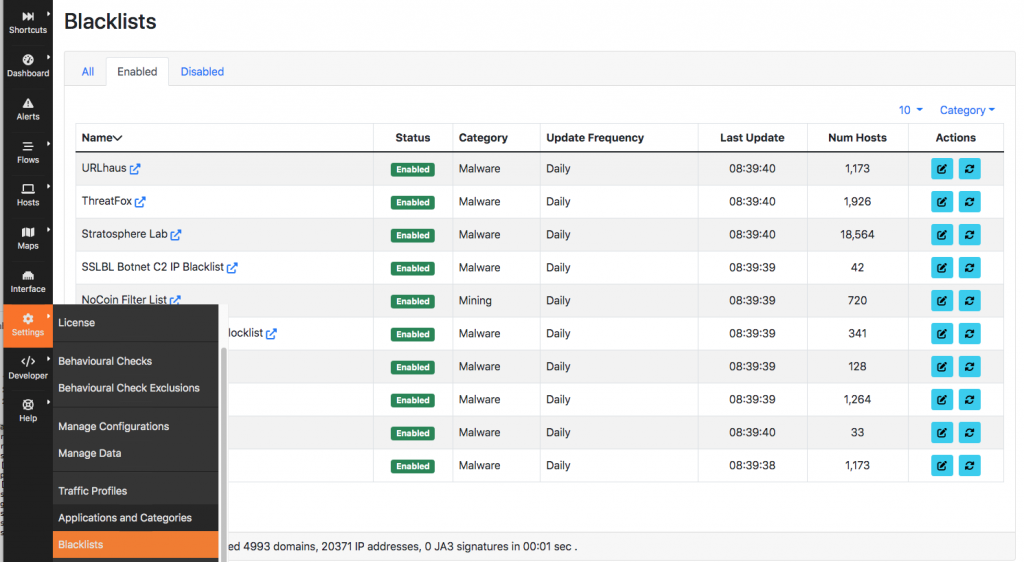
In ntopng you can specify what blacklists to use using the blacklist menu from the left sidebar.
ntopng comes with various high-quality built-in blacklists that are periodically refreshed by ntopng. In fact it is very important to:
- Refresh blacklists periodically as outdated information can lead to false positives.
- Use high-quality blacklists as they are constantly updated by professionals.
As said above, you can create your own blacklist and upload it into ntopng. All you need to do is to go to /usr/share/ntopng/httpdocs/misc/lists/custom and create a custom configuration file such as
{"name":"MyBlackList","format":"ip","enabled":true,"update_interval":86400,"url":"https://blacklist.local/myblacklist.csv","category":"malware"}
that instructs ntopng to daily download the custom blacklist from https://blacklist.local/myblacklist.csv that contains the IP addresses (one per line) that are supposed to be malware (or honeypots).
Whenever ntopng sees a flow that involves a host in a malware list, an alert is generated
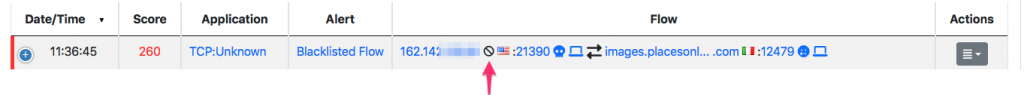 for such host, that can trigger an an action using the recipients/endpoint mechanism.
for such host, that can trigger an an action using the recipients/endpoint mechanism.
If you want to read more about blacklists in ntopng, please refer to the user’s guide.
Enjoy !