A slow DoS (Denial of Service) attack is a type of cyberattack designed to overwhelm a server or web application by exploiting protocol weaknesses—not through high-volume traffic, but by sending requests very slowly or keeping connections open as long as possible. This consumes server resources (like concurrent connection limits, memory, or threads) with minimal bandwidth usage by the attacker. Instead of flooding the target with huge amounts of data, the attacker sends legitimate-looking requests at an extremely slow pace, or sends partial requests and delays completing them.
The server keeps these connections open, waiting for the request to finish, which eventually exhausts its pool of available connections—blocking legitimate users. In short, a slow DoS attack denies service by making the server wait, not by flooding as a volumetric DoS/DDoS (Distributed DoS).
Slow DoS attack include:
- Slowloris: Opens many HTTP connections and sends headers slowly or sends partial requests, never completing them.
- Slow POST/GET Attack: Sends a legitimate POST transmitting the body extremely slowly, or do a GET from the server but reads the response very slowly, keeping the connection alive and consuming server memory.
Unfortunately these attacks are more common than what most people think, and in the last weeks they are raising again. For this reason we have extended all our tools to detect (ntopng, nProbe..) and block (ntopng Edge) these type of attacks. This has been implemented by defining a new flow risk in nDPI named Slow DoS. This is how it works.
If in your network you have suspicious SlowDoS flows, you can go in the “Live Flows” page and select in the status menu the flow connections.
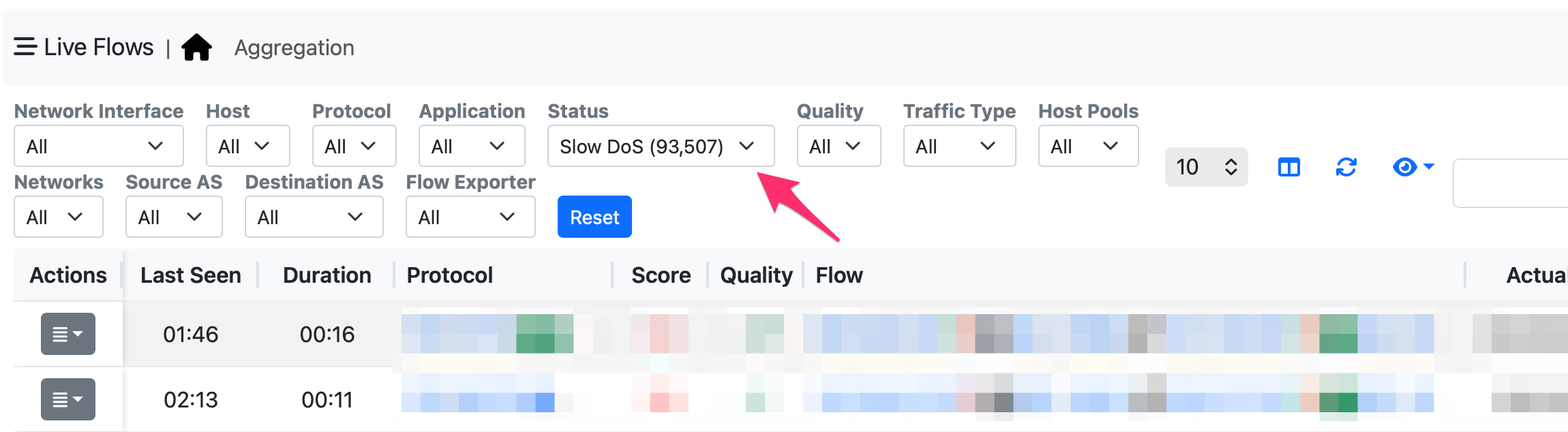
If you go in Actions -> Info you can see more information about the flow, and in the flow risk session you will see what is the problem that has been detected. Below you can see details of one of those flows who has been marked as SlowDoS because in this case past the TCP 3-way-handshake the server has to wait more than 10 seconds before the client issued the request.
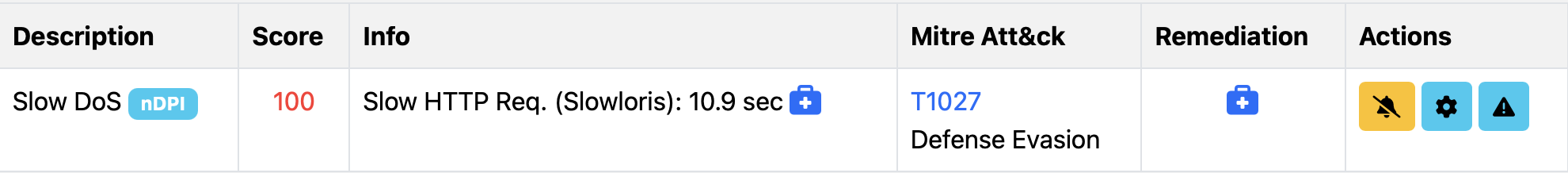
SlowDoS detection is not limited to clear-text protocols such as HTTP, but it also applies to TLS communications where detection works based on the analysis of TCP records.
In summary:
- Slow DoS attacks are raising again, both in clear-text and encrypted communications.
- You can use ntop tools such as ntopng or nProbe to spot SlowDoS attackers., or use ntopng Edge to block slow DoS flows.
Enjoy !
