Software Packet Filtering
Packet filtering is the ability to discard incoming packets. Pioneered by the popular BPF (Berkeley Packet Filter) used in all pcap-based applications such as tcpdump and wireshark, PF_RING has further extended this model by adding new types of filter (perfect and wildcard filters) for fine grained packet filtering. For instance you can decide to filter all UDP packets or only those HTTP packets sent by host X to server Y. We have written many paper on this subject you can find here.
If you want see how PF_RING filtering can be used, you have a look at the PF_RING User’s Guide, or explore the code of the demo applications we provide as example.
Hardware Packet Filtering
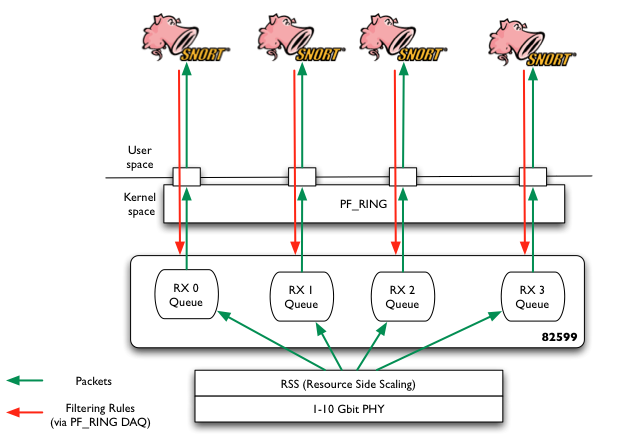
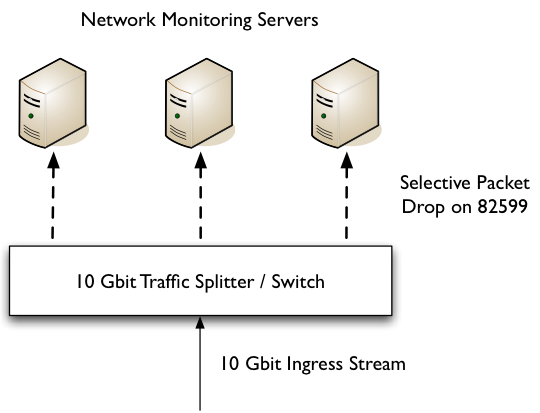
Many people don’t know that in order to filter packets in hardware, it is not necessary to spend a lot of money for purchasing costly FPGA-based network adapters. Intel 82599 and Silicom Director Card are able to filter packets in hardware with ability to specify thousand of filtering rules.
Unfortunately Linux does not allow you to easily play with hardware filters, thus often this feature is not used because people do not know how to access it. For this reason we have extended PF_RING for supporting hardware filters. This means that you application can set filters via the PF_RING API and if you own a NIC that supports hardware filters, by magic PF_RING sets those filters in hard are (and removes them when you kill the application that has set them.
Usage cases are countless, but security and traffic balancing/mitigation are definitively among those. You just need to find yours.