A blacklist is an access control mechanism which denies access to selected network resources to peers belonging to a curated list. Blacklists often represent the first line of defence for many networks as they can reduce internal hosts’ risk of establishing communications with peers with a bad reputation.
Many companies use blacklists for detecting malicious activities. In ntopng we use IP blacklists to label traffic exchanged with malicious peers.
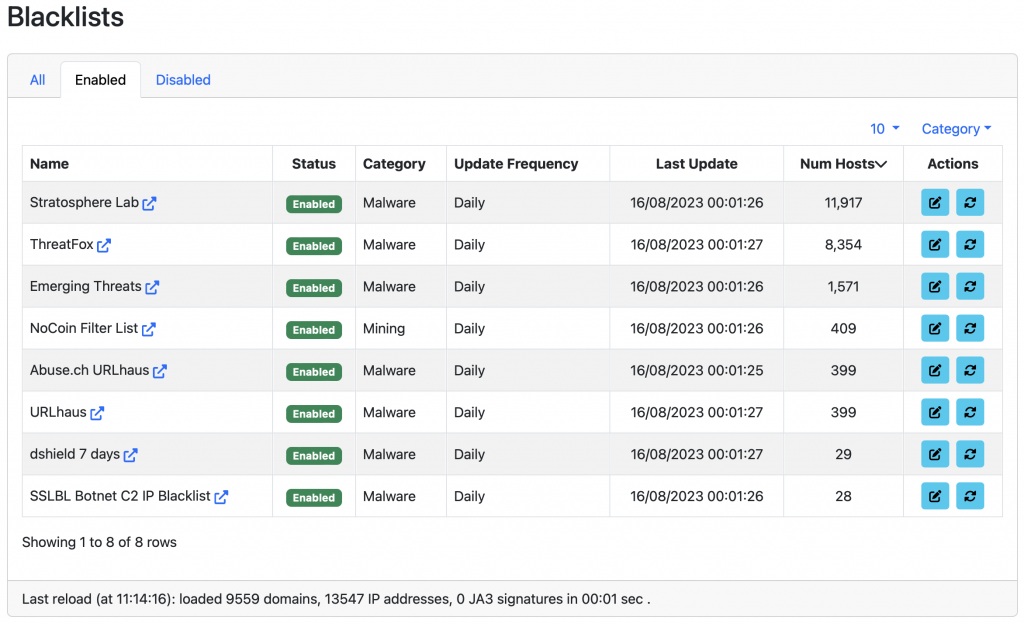
While the concept of blacklist is very simple and many people are familiar with it, we know very little of how such blacklists have bene created. In particular we have asked ourselves a few simple questions:
- How effective are publicly available IP blacklists when used on my network?
- Can I trust them to block traffic or they contain false positives?
- Are they outdated or they are updated regularly?
In order to answer to the above questions, we have made a large scale study whose goal was to assess publicly available blacklists. The result of this study are presented in this paper that was presented at 6th International Workshop on Cyber Security (CSW-2023). Those who have no time to read the paper can glance through the presentation slides. The conclusions of the study are:
- Blacklists can only capture a small fraction of scanning activities, and the recall does not significantly improve when blacklists maintained by distinct parties are combined.
- Blacklists are optimised for precision, leaving much of the malicious traffic undetected and a false sense of security.
Bottom line: it’s time to create our own community-powered blacklists.
Stay tuned for details !
