Earlier this month a new highly evasive malware attacker named SunBurst has been disclosed. Immediately some countermeasures have been disclosed and in particular some Snort/Suricata rules have been published. We have analysed the rules trying to figure out if ntop tools could detect and block Sunburst and the answer is yes, you can. Let’s have a look at some of the rules. The first thing you can observe is that the rules are any/any, meaning that an IDS has to look into every single connection this because most IDS do not use DPI as ntop tools do, hence they need to search everywhere instead of targeting the exact fields: this means that overall the tool performance is degraded as even traffic that is not relevant has to be analysed, and that you might encounter false positives.
The rules below
alert tcp any any <> any 443 (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"|16 03|"; depth:2; content:"avsvmcloud.com"; distance:0; sid:77600845; rev:1;) alert tcp any any <> any 443 (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"|16 03|"; depth:2; content:"|55 04 03|"; distance:0; content:"digitalcollege.org"; within:50; sid:77600846; rev:1;) alert tcp any any <> any 443 (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"|16 03|"; depth:2; content:"|55 04 03|"; distance:0; content:"freescanonline.com"; within:50; sid:77600847; rev:1;)
are basically a TLS SNI (Server Name Indication) match.
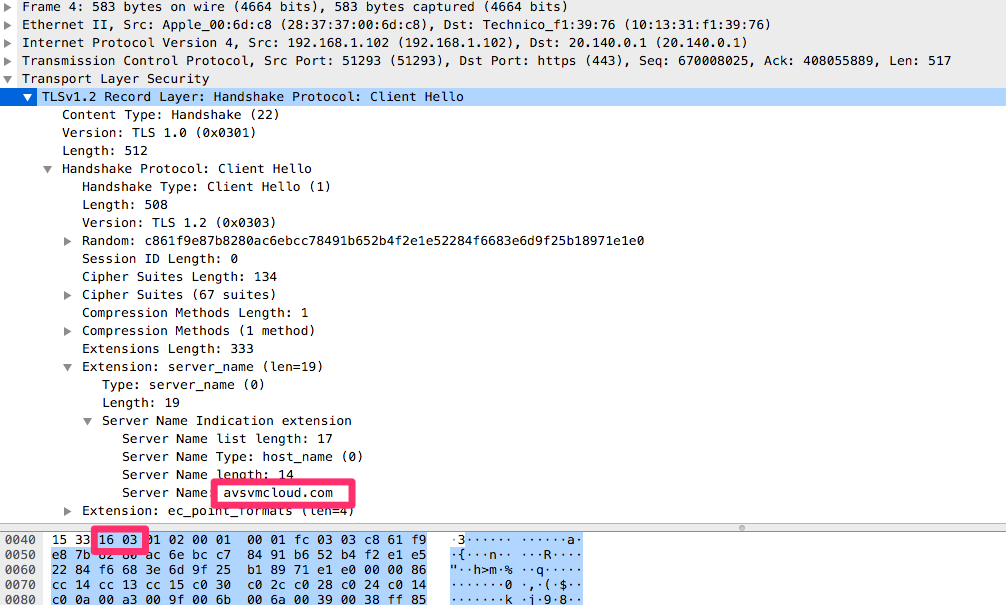
that you can detect with nDPI.
Note that such rules are suboptimal as they have been designed before encrypted traffic was used, and so they are very primitives and limited in scope. See for instance what DPI reports for such TLS traffic
TCP 192.168.1.102:51293 <-> 20.140.0.1:443 [proto: 91/TLS][cat: Web/5][7 pkts/998 bytes <-> 6 pkts/1553 bytes][Goodput ratio: 52/74][1.74 sec][ALPN: h2;http/1.1][bytes ratio: -0.218 (Download)][IAT c2s/s2c min/avg/max/stddev: 0/109 253/420 1142/1033 447/434][Pkt Len c2s/s2c min/avg/max/stddev: 66/66 143/259 583/1215 180/428][Risk: ** Self-signed Certificate **][TLSv1.2][Client: avsvmcloud.com][JA3C: 2a26b1a62e40d25d4de3babc9d532f30][JA3S: 364ff14b04ef93c3b4cfa429d729c0d9][Issuer: CN=localhost][Subject: CN=localhost][Certificate SHA-1: D2:D1:B8:2B:15:FB:C9:51:B7:24:FF:56:B4:EF:9D:82:E2:E5:EA:B3][Validity: 2020-10-14 21:20:12 – 2022-12-17 11:32:25][Cipher: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384][Plen Bins: 33,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,33,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,33,0,0,0,0,0,0,0,0,0,0,0,0]
As you can see this is a self-signed TLS certificate that is not a good thing either.
Other rules like these below are different but similar
alert tcp any any -> any any (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"T "; offset:2; depth:3; content:"Host:"; content:"freescanonline.com"; within:100; sid:77600852; rev:1;) alert tcp any any -> any any (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"T "; offset:2; depth:3; content:"Host:"; content:"deftsecurity.com"; within:100; sid:77600853; rev:1;) alert tcp any any -> any any (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"T "; offset:2; depth:3; content:"Host:"; content:"thedoccloud.com"; within:100; sid:77600854; rev:1;) alert tcp any any -> any any (msg:"APT.Backdoor.MSIL.SUNBURST"; content:"T "; offset:2; depth:3; content:"Host:"; content:"virtualdataserver.com"; within:100; sid:77600855; rev:1;)
In this case these rules basically say: search on HTTP (even on non standard ports) and in case you find connections towards specific sites (e.g. freescanonline.com) raise an alert.
In summary, these are old-style rules designed for year 2000 protocols that need to be refreshed. These are the equivalent rules for nDPI
$ cat sunburst.protos # Format: # <tcp|udp>:,<tcp|udp>:,.....@ # Subprotocols # Format: # host:"",host:"",.....@ # # IP based Subprotocols # Format: # ip:,ip:,.....@ host:"avsvmcloud.com"@APT.Backdoor.MSIL.SUNBURST host:"digitalcollege.org"@APT.Backdoor.MSIL.SUNBURST host:"freescanonline.com"@APT.Backdoor.MSIL.SUNBURST host:"freescanonline.com"@APT.Backdoor.MSIL.SUNBURST host:"deftsecurity.com"@APT.Backdoor.MSIL.SUNBURST host:"thedoccloud.com"@APT.Backdoor.MSIL.SUNBURST host:"virtualdataserver.com"@APT.Backdoor.MSIL.SUNBURST
and you can now start ndpiReader as follows
$ ndpiReader -p sunburst.protos -i ~/avsvmcloud.com.pcap -v 2 ... Detected protocols: APT.Backdoor.MSIL.SUNBURST packets: 13 bytes: 2551 flows: 1 Protocol statistics: Acceptable 2551 bytes JA3 Host Stats: IP Address # JA3C 1 192.168.1.102 1 1 TCP 192.168.1.102:51293 <-> 20.140.0.1:443 [proto: 91.255/TLS.APT.Backdoor.MSIL.SUNBURST][cat: Web/5][7 pkts/998 bytes <-> 6 pkts/1553 bytes][Goodput ratio: 52/74][1.74 sec][ALPN: h2;http/1.1][bytes ratio: -0.218 (Download)][IAT c2s/s2c min/avg/max/stddev: 0/109 253/420 1142/1033 447/434][Pkt Len c2s/s2c min/avg/max/stddev: 66/66 143/259 583/1215 180/428][Risk: ** Self-signed Certificate **][TLSv1.2][Client: avsvmcloud.com][JA3C: 2a26b1a62e40d25d4de3babc9d532f30][JA3S: 364ff14b04ef93c3b4cfa429d729c0d9][Issuer: CN=localhost][Subject: CN=localhost][Certificate SHA-1: D2:D1:B8:2B:15:FB:C9:51:B7:24:FF:56:B4:EF:9D:82:E2:E5:EA:B3][Validity: 2020-10-14 21:20:12 - 2022-12-17 11:32:25][Cipher: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384][Plen Bins: 33,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,33,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,33,0,0,0,0,0,0,0,0,0,0,0,0]
Now you can use this technique in other tools such as ntopng as follows
ntopng -p sunburst.protos -i ~/avsvmcloud.com.pcap
Then inside ntopng you have to tell it that Sunburst is a malware by binding (menu Settings -> Applications and Categories) that Sunburst belongs to the malware category.
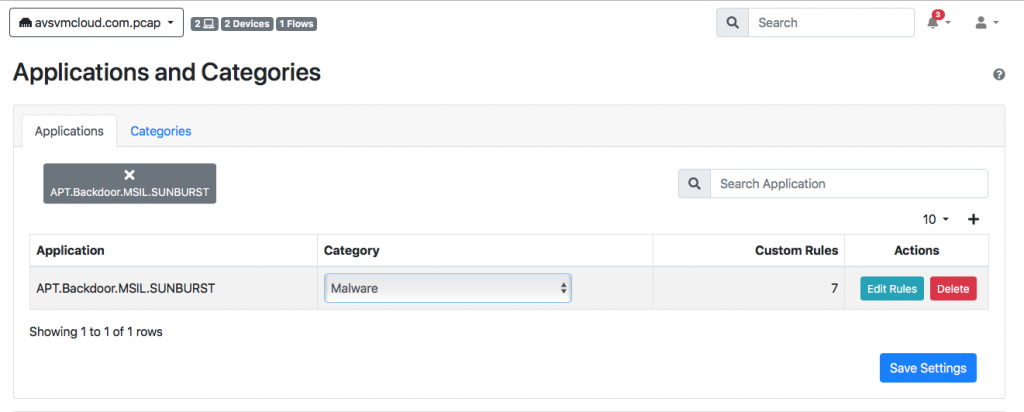
Done that ntopng detects it as a malware
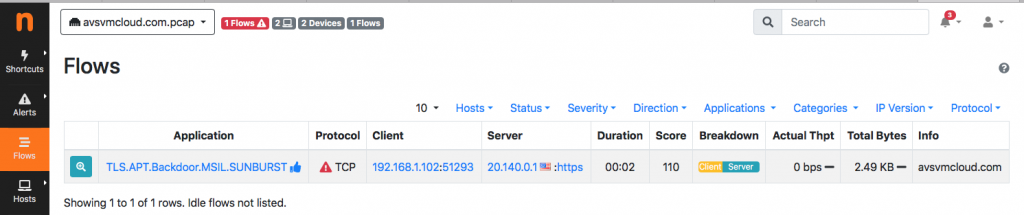
and triggers an alert
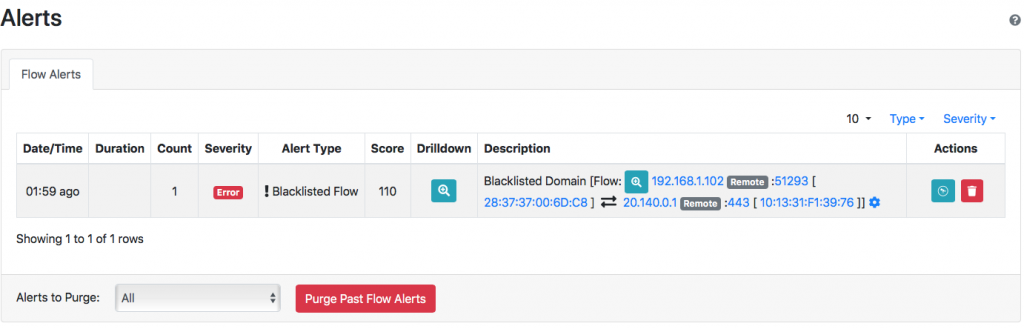
that can be sent via the endpoint/recipients mechanism to external applications, messaging apps, ElasticSearch or SecurityOnion.
If in addition to detecting you want also to block it, just use ntopng Edge (that is basically ntopng inline) and you’re done.
Enjoy !
