A VLAN is a method for partitioning a layer two broadcast domain creating virtual networks of homogeneous systems hence promoting network segmentation. A ethernet port with no VLAN tag is called access port, whereas a switch port with VLAN-tagged packets is called tagged or trunk port. End systems are usually connected to access ports meaning that they deal with untagged packets that are then marked by the switch according to the VLAN port configuration. For this reason a end system is not aware of the VLAN id that is used to mark its traffic (if any). Traffic (e.g. using a port mirror or a network tap) on a non-access port is instead VLAN tagged (sometimes VLAN tags are stacked) hence monitoring systems need to properly handle VLAN tagged traffic.
The Problem
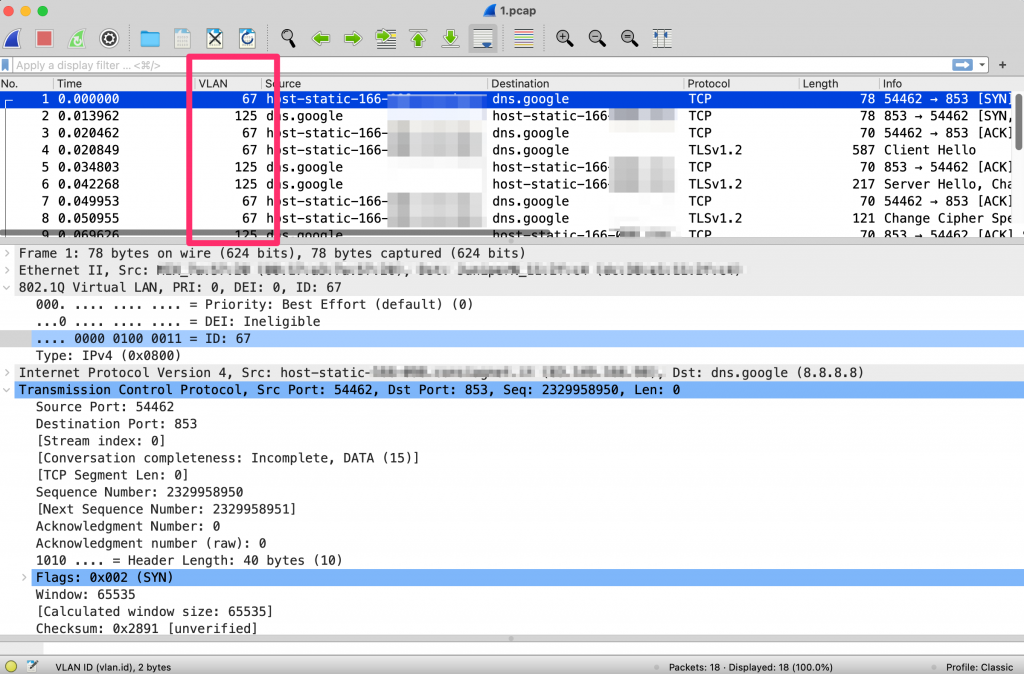
Based on the network topology and how traffic is wiretapped, it is not uncommon to observe asymmetric VLAN tags. In the figure below it is shown traffic exchanged by two hosts with two different VLAN IDs: 67 for traffic client to server, and 125 for traffic server to client.
It is worth to remark that:
- The client is attached to an access port and thus the traffic when close to the client port will have the same VLAN Id (that can be 67, 125 or even another VLAN Id) for the RX and TX directions. This is to make sure that the two directions are merged on the same port.
- When the traffic leaves the network and hits the Internet, the VLAN tag is stripped and traffic is sent untagged (i.e. the VLAN Id is a local network concept that is not propagated to the Internet).
This said, in most cases wiretapping VLAN-tagged traffic has symmetric VLAN IDs (in the above case both client-to-server and server-to-client traffic have the same VLAN Id) but in some cases tags are asymmetric (i.e. each direction has a unique VLAN ID) as in the above case. Flow-based applications such as ntopng and nProbe will not classify the above traffic as a single flow, but with two unidirectional flows as the VLAN ID is different. This has also as consequence that nDPI will partially work as only one side of the communication is observed per flow.
Solution
In order to harmonise the traffic reconciling the two traffic directions into a single flow, ntop applications have the ability to “ignore” the VLAN tag Id in the flow key (i.e. the traffic is handled as untagged traffic with no VLAN tag at all).
ntopng
In ntopng there is a command line option “–ignore-vlans” for ignoring at all VLAN tags in traffic.
Example: ntopng -i eth1 –ignore-vlans
nProbe
In nProbe there is even more flexibility for ignoring specific fields and not just the VLAN Id. Please note that in nProbe it is possible to selectively ignore the inner and outer (in case of IEEE 802.1 ad) VLAN tags.
[--aggregation|-p] <aggregation> | It specifies the flow aggregation level:
| <OuterVLAN>.<InnerVLAN>/<proto>/<IP>/<port>/<TOS>/<SCTPStreamId>/<exporterIP>/<ICMP>
| where each element can be set to 0=ignore
| or 1=take care.
Example: nprobe -i eth1 -p 0.0/1/1/1/1/1/1/1
Conclusion
Asymmetric VLAN-tagged traffic is not uncommon on large networks. If not properly handled, network measurements are not correct as flows are asymmetric with partial DPI. In this article we have shown how to configure both ntopng and nProbe to ignore VLAN tags and thus reconcile monitored traffic.
Enjoy !