One of the main limitations of flow-based protocols such as IPFIX and NetFlow is that the traffic is sent in cleartext. This means that it can be observed in transit and that it is pretty simple to send fake flow packets that can then pollute the collected information. As of today, unencrypted protocols need to be avoided and thus some workarounds to this problem need to be identified. Often people use VPNs to export flows, but this is not a simple setup with cloud services or on complex networks, so people sometimes rely on ACL (Access Control List) which does not address privacy and integrity concerns.
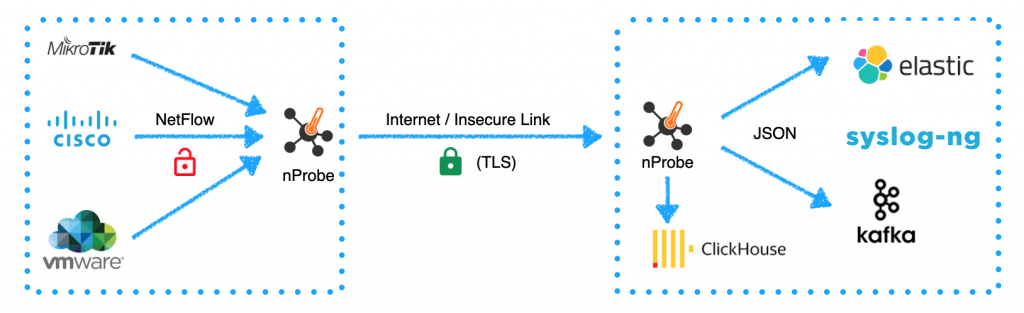
As shown above, this article shows you how to use TLS with nProbe in order to implement secure flow collection and export. All you need is nProbe (dev) that can collect export flows over UDP/TCP/SCTP (export only on Linux), and now over TLS. All you need to do is to use the method with command line options –collector-port (flow collection) and –collector (flow export). Examples:
- Suppose you want to collect flows over UDP on port 2055
–collector-port udp://2055 - Suppose you want to collect flows over TCP on port 2055 on localhost
–collector-port tcp://127.0.0.1:2055 - Suppose you want to export flows to remote collector 192.168.1.2 over TLS on port 2055
–collector tls://192.168.1.2:2055
When collecting flows, nProbe opens the specified port and listens for TLS connections. In this setup it is necessary to provide a TLS certificate and private key that you can generate with services such as Let’s Encrypt or using a self-signed certificate that you can generate with
openssl req -x509 -nodes -newkey rsa:4096 -keyout key.pem -out cert.pem -sha256 -days 365
that can be passed to nprobe with –tls-priv-key and –tls-cert command line options. A complete example of nProbe collecting flows over TLS on host mycollector.ntop.org port 2055 is:
nprobe --tls-priv-key key.pem --tls-cert cert.pem -n none -i none --collector-port tls://mycollector.ntop.org:2055
You can now connect your remote nProbe capturing packets on eth0 and exporting flows to the above collector using the command below:
nprobe -i eth0 --collector tls://mycollector.ntop.org:2055
Note that nProbe verifies the TLS certificate, so:
- You need to make sure that you use a hostname and not an IP address when specifying your collector IPs
- Expired, self-signed, or insecure certificates are not accepted. In this case, you can force nProbe to ignore the above issues when connecting to a remote collector adding –tls-insecure. Example:
nprobe -i eth0 --collector tls://192.168.2.243:2055 --tls-insecure
Finally do not forget that for a long time Probe can deliver via ZMQ flows in a secure and encrypted format to ntopng.
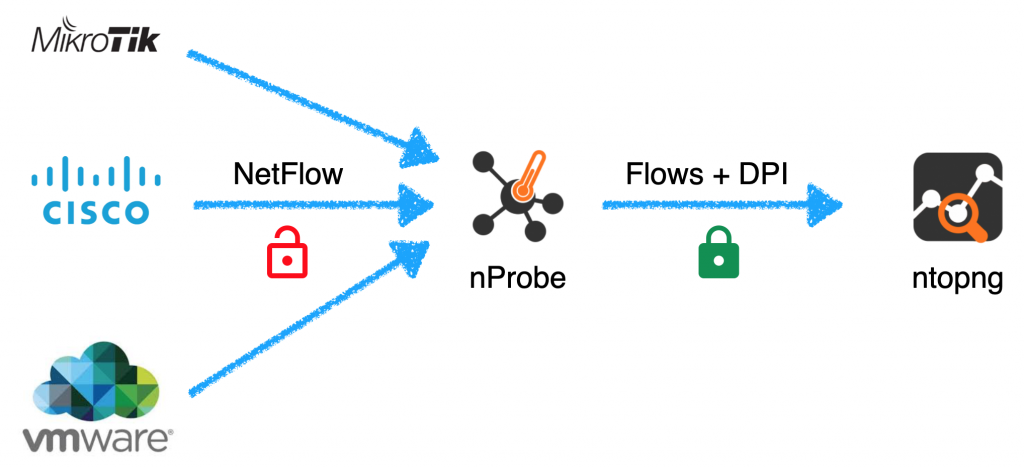
If you want to read more about nProbe and TLS, please refer to the user’s guide.
Enjoy !
