nProbe IPS is an inline application able to both export traffic statistics to NetFlow/IPFIX collectors as well to ntopng, and enforce network traffic using nDPI, ntop’s Deep Packet Inspection framework. This blog post shows you how you can use a new graphical configuration tool we have developed to ease the configuration of IPS rules on OPNsense. Please note that nProbe IPS is also available on pfSense and Linux where you need to configure it using the configuration file as described later in this post and in the nProbe user’s guide.
Once installed nProbe as described in this page, you will see nProbe listed in the Services page as depicted below.
nProbe can be use in two operational modes:
- IPS mode: nProbe will operate in inline mode, meaning that packets are received by nProbe that based on the policy rules will decide if they can be forwarded or blocked.
- Passive mode: nProbe will observe the traffic flowing on the selected interface without interfering with the packets that flow on the monitored interface.
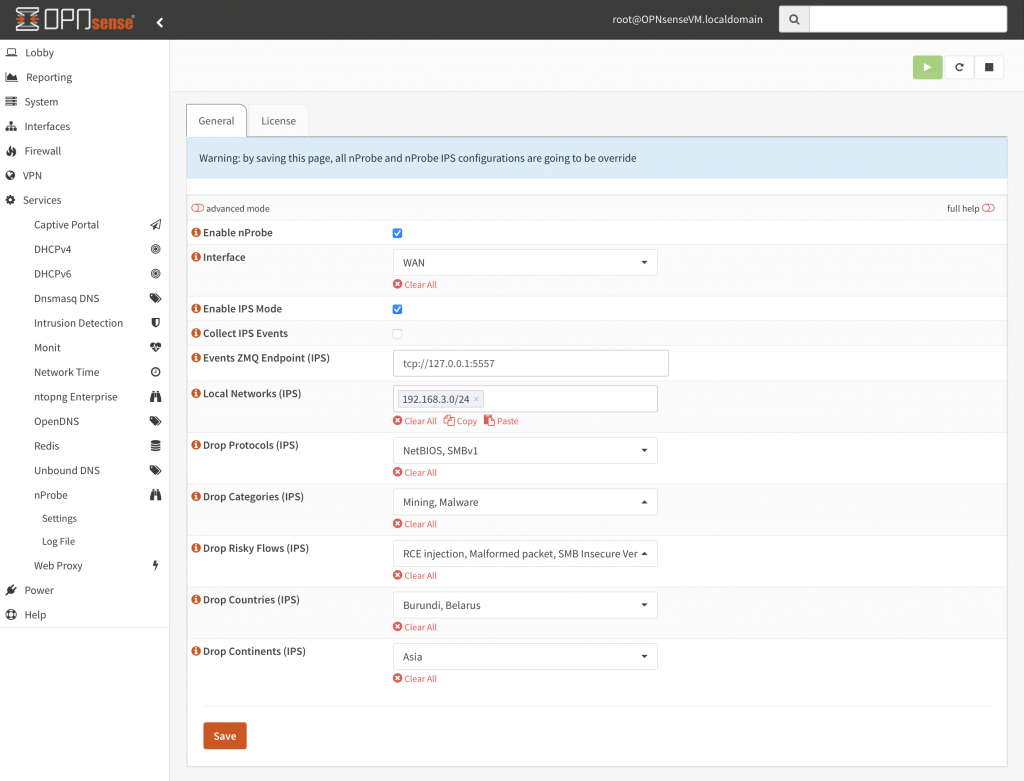
Enabling IPS Mode
The Interface dropdown menu allows network administrators to specify what interface nProbe will supervise. As we need to block traffic, IPS mode needs to be enabled by selecting the “Enable IPS Mode” checkbox. If you enable ntopng (either on the OPNsense box or on another host) you can specify an optional ZMQ endpoint towards which ntopng will send events to nProbe: you can read more about integrating ntopng and nProbe IPS on the user’s guide.
IPS rules are enabled only on traffic matching one of the peers specified in the “Local Networks” field. This means that if you have a connection host A: port a <-> host B:port b flowing on the specified network interface, such connection will be enforced only if at least one of the peers (either host A, or host B) is specified in the local network list. If no peer is part of the network list, such flow will not be enforced and will flow without restrictions. This way, you can decide what traffic needs to be enforced, and what traffic needs to flow unpoliced.
Configuring IPS Policies
The default IPS configuration is set to Allow, meaning that nProbe will not block any packet. Through the user interface you can specify what traffic needs to be blocked. In particular you can specify:
- The list of application protocols that can be blocked. They include popular protocols such as Facebook, YouTube, Netflix as well all the over 250 protocols supported by nDPI.
- Blocking traffic based on application protocols can be complicated for many people that are not familiar with network protocols. For this reason it is possible to specify protocol categories instead of the individual protocols. This facility can be used for fine grained tuning. For instance if you want to block all the social networks traffic, you can specify the “Social Network” category instead of selecting all the individual protocols such as TikTok, Pinterest or Snapchat.
- Specify the flow risks that need to blocked by the IPS. For instance, you can configure nProbe to drop encrypted connections with self-signed certificates, malformed packets or traffic containing clear-text credentials. You can use this feature to block traffic connections that contain some potential security risks that instead nProbe can block.
- The list of countries and continents forbidden to be contacted by local hosts. This way network administrators can prevents contacts with unwanted locations. A typical example is when you need to protect some resources based on location, for instance allowing servers from being accessed only by hosts located inside the local country.
Once policies are saved, they are immediately effective and with no need to restart the nProbe service.
The OPNsense user interface has been developed to simplify the policies configuration, but if you are an advanced user or if you do not run OPNsense (e.g. pfSense or Linux), you can still configure policies by editing the IPS configuration file located under /usr/local/etc/nprobe (on Linux on /etc/nprobe). This way you can specify more fine grained configuration by enabling multiple configurations as specified in the nProbe user’s guide.
Final Words
nProbe IPS is a versatile traffic policed based on deep packet inspection. It can complement the native firewall by adding the ability to drop traffic based on application protocols, cyber security risks, and geofencing. Enjoy !
