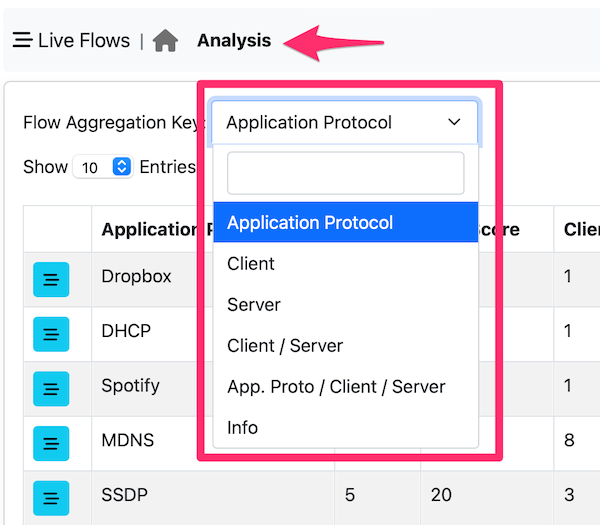
Traditionally flow-based tools are based on the 5-tuple attributes (source and destination IP, source and destination port and the protocol field). Often they are complemented with additional attributes such as VLAN or Tunnel Id in order to avoid mixing in the same flow packets that belong to different communications.
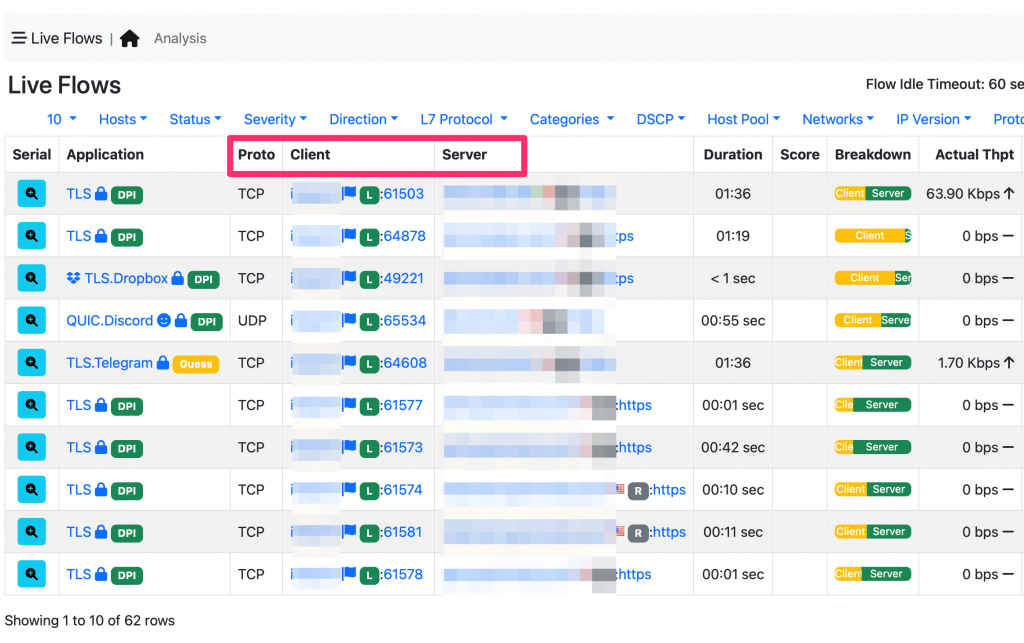
The above picture shows the 5-tuple key in the live flows window. Looking at flows using the 5-tuple makes sense if we want to understand what it is happening at the individual flow level, but it makes difficult to understand the big picture and answer to questions such as:
- What are the top client-server conversations?
- What are the flows of the most used application protocols?
- What host has the highest number of incoming flows?
- What are the flows towards weather-data.apple.com ?
In order to answer these questions we have developed a new entry called Live Flows Analysis that you can find in the menubar
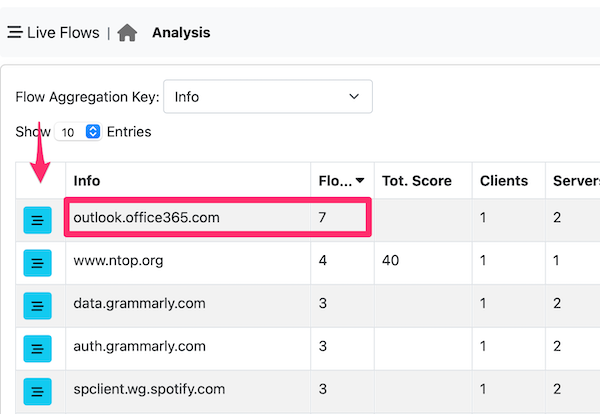
Using it you can now select the aggregation criteria for merging reporting flows no longer as 5-tuples, but according to the criteria you selected. This allows you to manipulate flows in an aggregated format and then by clicking on the blue flow icon, show the flows what have been aggregated. For instance suppose you want to count flows that are going towards towards outlook.office365.com. All you need to do is to select Info as criteria (this way you should not worry if outlook.office365.com resolved to different IP addresses as they will all be grouped under the same name) then the flow count column shows that you have 7 flows.
If you want to see such flows, all you need to do is to click on the flow icon of the first column and see all the flows, this time using the 5-tuple
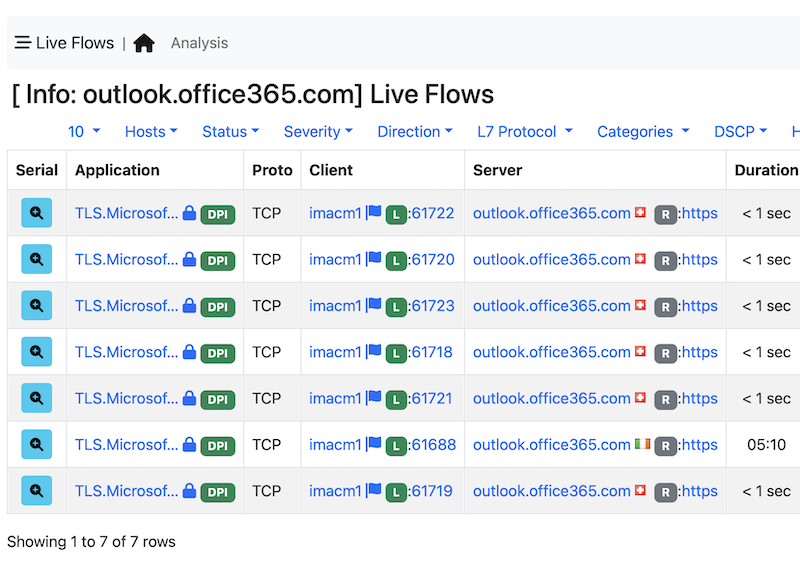
You can do the same with the other criteria currently supported (more will come in the near future): namely aggregate, search, sort and the drill down.
Enjoy !