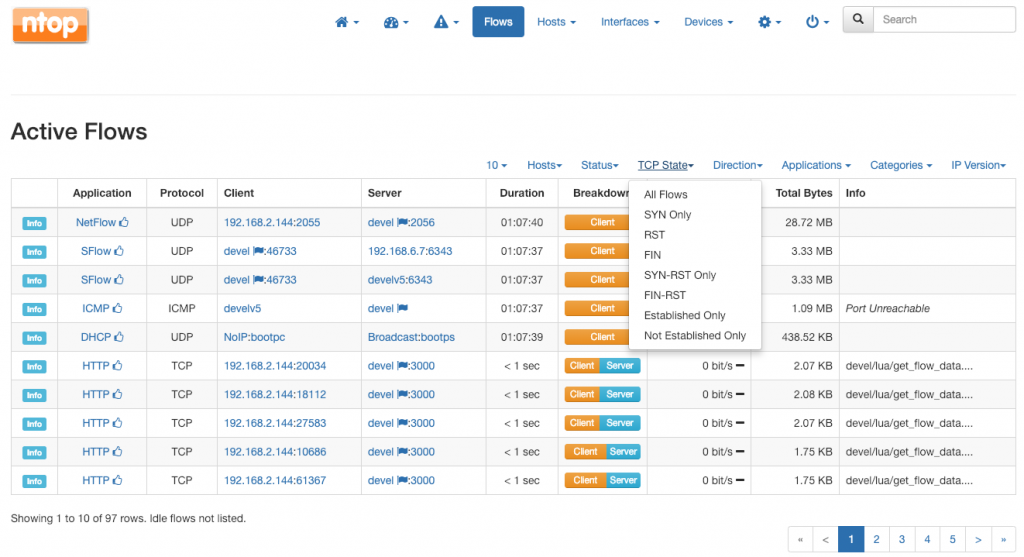
Starting from the latest 3.9 version, ntopng features and handy dropdown menu that allows you to filter flows on the basis of their current TCP state.
Being able to filter flows on the basis of their TCP state is particularly useful as it allows to separate the normal flows from those that are suspicious or symptomatic of certain network issues. For example, one can unveil:
- Flows that only have a client SYN. This can identify clients attempting to connect to a server that is no longer responding (down?) or misbehaving hosts that are performing SYN-scans.
- SYN-RST only flows. In general, when a client sends a SYN and immediately gets a RST from the server, it means that the server port the client has tried to connect to is closed. Such RST could signal a server application that is no longer working (down?) but it could also highlight misbehaving hosts that are performing port scans.
- Not established flows. Such flows are all those flows that are not ready to exchange data. They can be FIN-ned or RST-ted flows, or flows that have still to complete the initial three-way handshake.
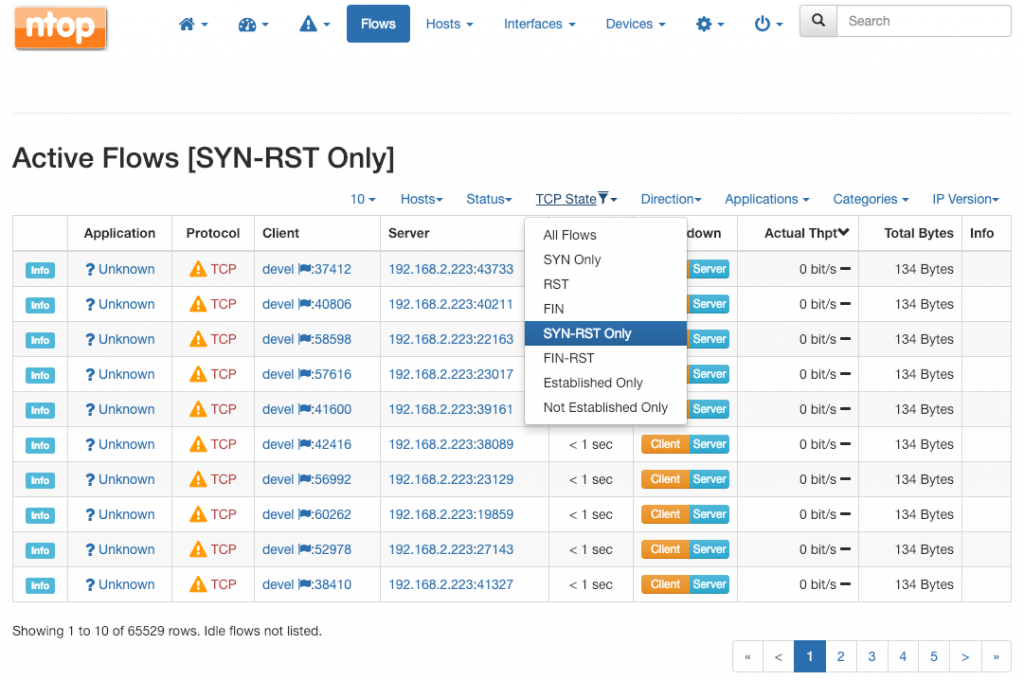
For example, running a port scan with nmap as
simone@devel:~$ nmap -p- 192.168.2.223
Causes scanned host 192.168.2.223 to respond to devel with 65k+ RST as the majority of its ports are closed. In this case, highlighting such flows is as easy as picking the SYN-RST Only dropdown entry.
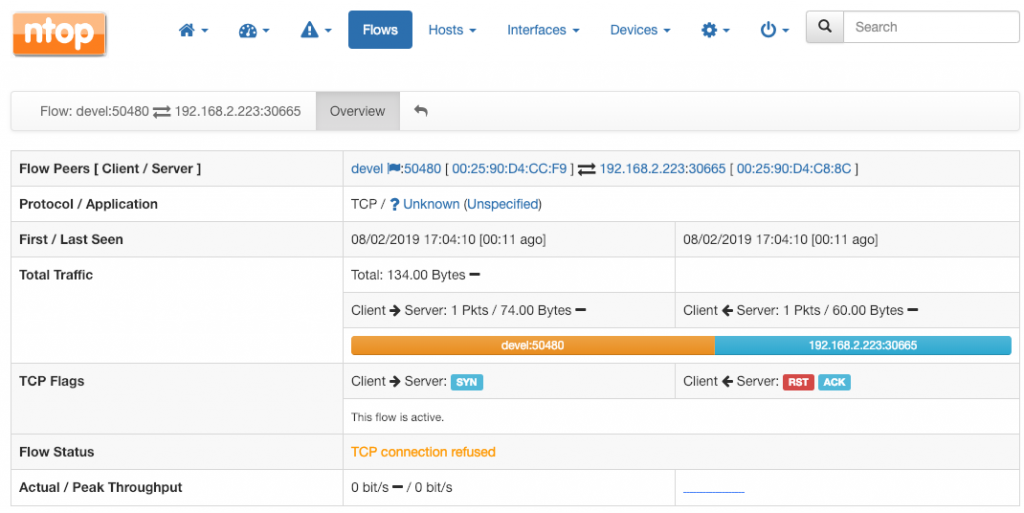
Selecting each of the listed flow will actually confirm the client has sent a SYN to the server which, in turn, has ACKnowledged the SYN and has RST-ed the connection.