Ongoing health emergency demands business to enable employee work from home: call it smart working or (better) remote working. This process puts pressure on the company Internet connection as many (if not all) the activities need to be done remotely. Working from home is a good practice in order to avoid extra personal stress and reduce virus spread, this only if company’s Internet lines have enough capacity to handle all the remote workers.
How can you measure this extra traffic (with respect to days before the emergency) and optimise your infrastructure? Now this is possible deploying ntopng on your company network. Simply enabling the syslog export from your VPN Concentrator and having the right ntopng version (this feature is implemented in the current development version of ntopng) you can do that: you could be enabled to verify in real time what’s your remote workers are doing, in a ntopng fashion.
For example you can do assurance of remote workers traffic, performance, behaviours and all the other things ntopng allow for traffic analysis. Starting from version 4.0 you can not only visualize the actual traffic ntopng is analyzing, but you can correlate also the trusting level of the traffic and measuring it with extra level of confidence: black listing, encryption level, behavior score, etc etc. As described in the users guide, you can define a syslog interface and specify the log producer configuration.
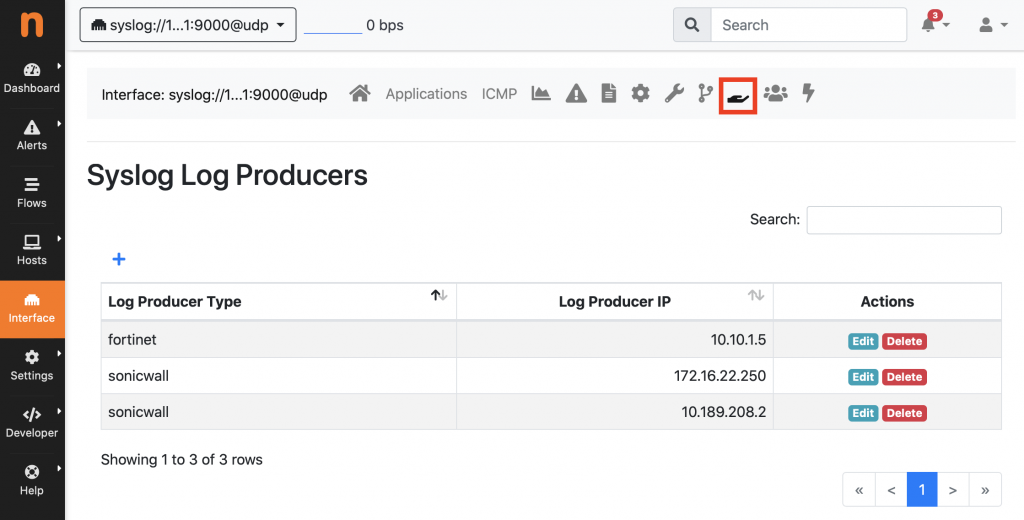
For instance in the above example the system collects flows from three different devices each with a different vendor configuration. Thanks to this ntopng is the main place to control and visualize your network health status, not only with mirrored interfaced, but with help of external feeds such as nprobe and syslog:
- nProbe can collect local or remote device traffic in order to be visualized and tracked via ntopng panel.
- syslog enables ntopng to correlate remote VPN username with a network address.
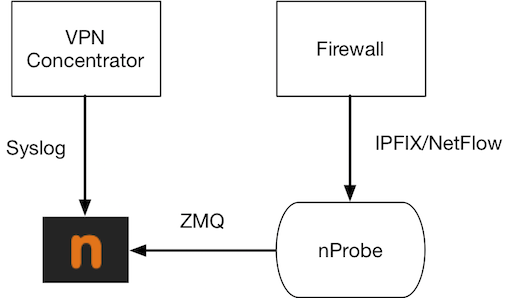
Let’s now consider a simple scenario: the firewall that segment the network send flows to ntopng and nprobe that accept syslog from VPN Concentrator.
Components
- Firewall. It export sFlow/nFlow/IPFIX to nProbe that send them in ZMQ format to ntopng.
- VPN Concentrator. It send syslog to ntopng.
- ntopng aggregate flows and correlate VPN IP Addresses with remote Username
- nprobe collect firewall flows and send them to ntopng via ZMQ.
Our Monitoring Goal
- Do assurance of firewalled traffic, this starting from remote users.
- Have historical and statistical data about VPN Users and firewall flows.
- Optimises the bandwidth based on monitored metrics.
Don’t forget that if you have multiple branches or location you could reach the same goals deploying remote nProbe instances to collect local traffic, and send it to central ntopng in encrypted way without NAT boundaries.
In other words, there are no technical limitations to the solution but only limits that you don’t want to overcome. Do you need more info? Feel free to contact us.
