Most people are used to top X: top senders, top receivers, top protocols. So in essence they are looking for elephants. While this is a good practice, mice are also very interesting as they can often be hidden in the noise. In cybersecurity noise is very good for attackers as they often try to hide themselves on it; this is in order to escape security. Many malware are programmed on a for loop fashion: do a), do b) do c) then go back to a) on an infinite loop. In essence this is a periodic activity that is worth to be investigated (see similar studies on this subject [1], [2], [3], [4]), but the standard top X analysis tools fall short in detecting it, so we need something more sophisticated. For this reason we have implemented a new feature in ntopng that can detect this behaviour and many other things.
In order to enable this feature, you need a recent version of ntopng (this feature is present only in the enterprise edition dev builds and it will be integrated in the next stable release), and enable the corresponding preference.
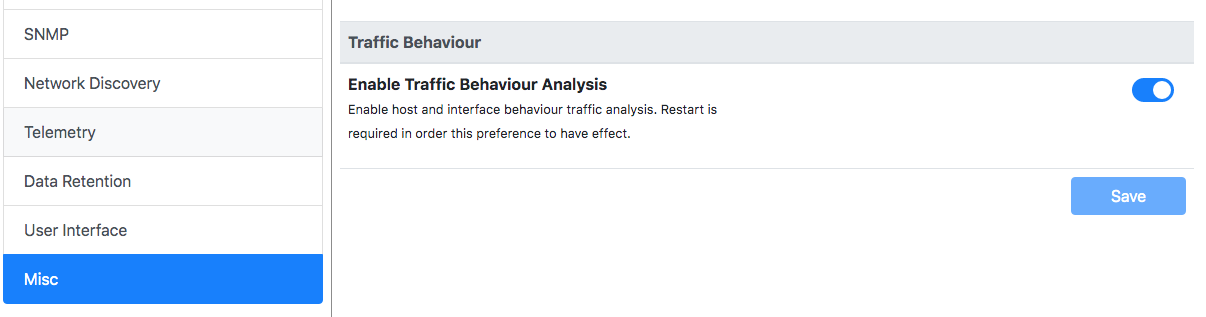
then you need to restart ntopng and wait until it detects some periodic behaviour is detected.
How Periodic Traffic Detection Works
A traffic is considered to be periodic if it repeats regularly over time with a specified frequency. Periodicity is not computed at flow level as ephemeral ports will jeopardise the work, but on a triplet <L4 protocol, IP source, IP destination/SNI>. In particular the SNI is very relevant to detect periodicity on cloud services where the same SNI is served by different server IP addresses. In order to avoid generating too much noise, multicast and broadcast destination IP addresses are ignored as in LANs there are many periodic services that might confuse network analysts. ntopng accounts triplets and determines the frequency based on the flow creation time. Some flows can have a frequency of 1 minute, others of one hour: ntopng will detect it automatically without people having to configure anything. Little frequency drifts are handled automatically and accounted by ntopng.
A triplet is marked as periodic with a given frequency, if ntopng has been able to observe it at least 3 times with a stable frequency (i.e. if the frequency is 1 hour you need to wait about 3 hours before ntopng reports you anything). In order to limit memory usage, ntopng accounts periodicities up to one hour but future versions can raise this limit that is set only to limit memory usage and not an algorithm limitation. If ntopng detects periodic traffic, this information is reported on the user interface under the interface page
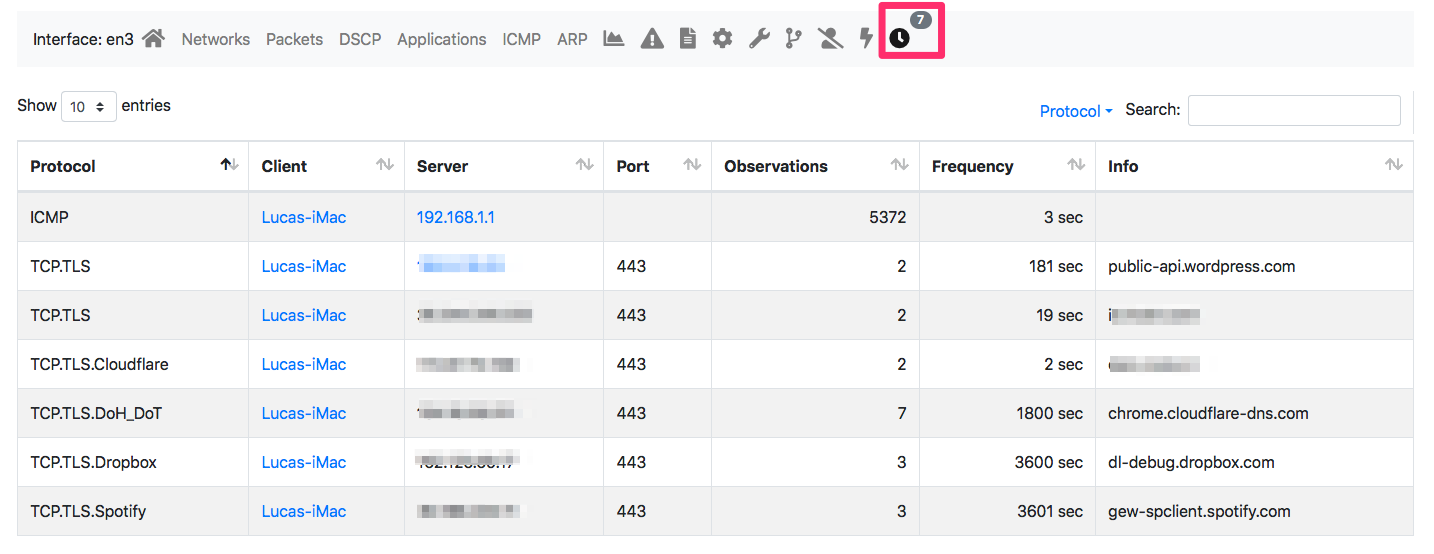
As you can see the application protocol, ports and frequency are reported.
Using Periodicity to Detect Threats
Not that you know more about periodic traffic you might wonder if this is just curiosity or more than that. Have a look at these two images below.
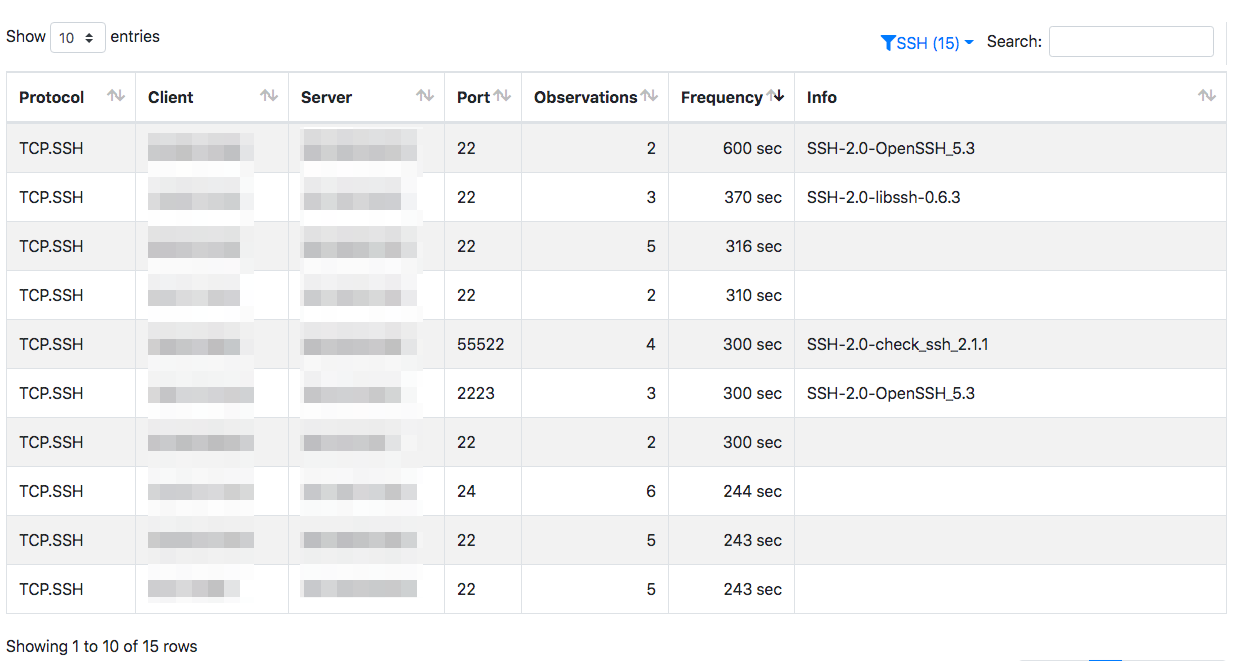
Let’s analyse the SSH traffic to see what is happening. As you can see ntopng has detected periodic communications that we pretty suspicious. this in particular if you look at the SSH ports, some of which are not standard. They can hide monitoring applications or other some kind of nasty behaviour
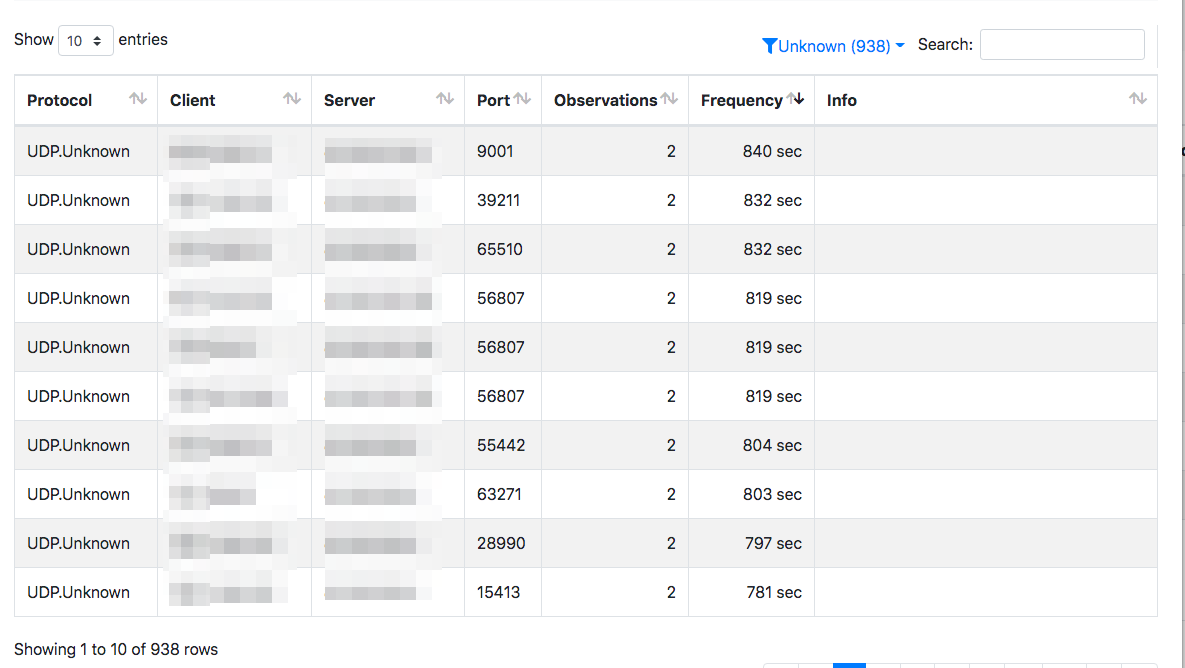
Interesting information can also come from Unknown periodic traffic (you could do the same looking at other protocols such as IRC for instance that are often used by malwares) is is very suspicious.
We hope you can find interesting insights on your network using this new feature. We plan to extend it with alerts, that can help network analysts to do in-depth analysis without having to deep dive into periodic data that can be pretty large for a big network.
Enjoy!
