NetFlow/IPFIX specifications have not considered privacy and confidentiality important. Exported flows are sent over unencrypted channels that prevent them to be exchanged on public networks unless techniques such as VPNs are used. Today encryption is no longer an option, and thus we have added encryption support in all our tools when flows are exchanged over ZMQ channels (e.g. when nProbe sends flows to ntopng). In order to use encryption a private/public keypair needs to be generated on the collector side (i.e. ntopng) and configured on all the probe applications sending flows to ntopng (e.g. nprobe or cento). In order to do this, the following steps needs to be performed:
- Start ntopng adding the
--zmq-encryptionoption. This option will generate, if not existing, the encryption keypair for all configured ZMQ interfaces. - Connect to the ntopng web gui and select the ZMQ interface information page and copy the value you have to put in
--zmq-encryption-key <...>parameter
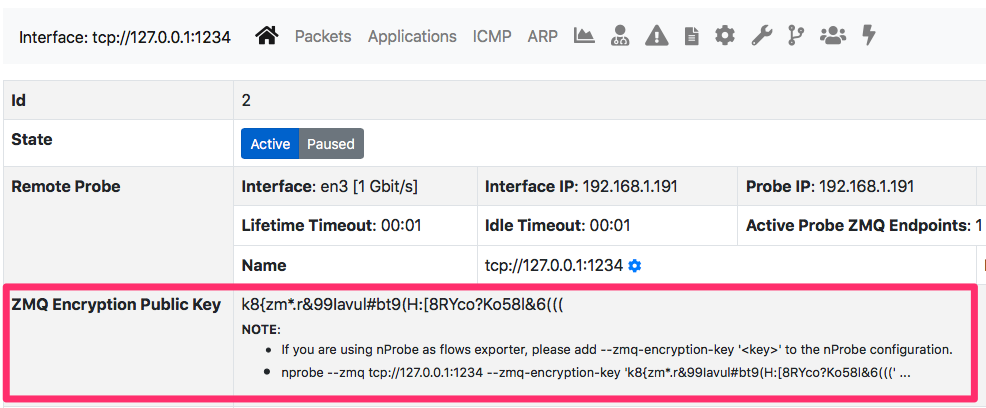
- Start nprobe sending flows to the collector ZMQ interface according. In the above example something like
nprobe --zmq tcp://127.0.0.1:1234 --zmq-encryption-key 'k8{zm*.r&99Iavul#bt9(H:[8RYco?Ko58l&6(((' -i ethXwill do the job
As ZMQ keypairs are generated per interface, you need to make sure that the pair <nprobe, ntopng> will use the same encryption key values for the same ZMQ interface.
Note:
- If you have multiple ZMQ interfaces, each interface will have a different keypair that you need to configure on the corresponding probe.
- Data encryption is currently available in nightly builds and will be included in the next stable release.
You can now safely exchange flows over public networks overcoming the limitations of NetFlow/IPFIX.
Enjoy!
