Trickbot is a malware distributed via malspam, spam emails containing links for downloading malicious files that infect computers. A pcap file of a trickbot infection named 2019-09-25-Trickbot-gtag-ono19-infection-traffic.pcap can be downloaded at this URL. You can analyse the file using nDPI as follows
ndpiReader -i 2019-09-25-Trickbot-gtag-ono19-infection-traffic.pcap -v 2 -J > /tmp/trickbot.txt
Let’s now open the trickbot.txt file and search for “Risk”. This is a tag added to nDPI analysed flows when there is a non-zero security risk associated with the analysed traffic. Most problems include:
- Obsolete TLS protocol with self-signed certificate
TCP 10.9.25.101:49457 <-> 187.58.56.26:449 [byte_dist_mean: 119.838346][byte_dist_std: 53.974475][entropy: 4.786248][total_entropy: 2546.284046][score: 0.9964][proto: 91/TLS][cat: Web/5][10 pkts/1532 bytes <-> 11 pkts/2197 bytes][Goodput ratio: 64/73][26.63 sec][bytes ratio: -0.178 (Mixed)][IAT c2s/s2c min/avg/max/stddev: 0/0 3328/819 20084/4504 6493/1528][Pkt Len c2s/s2c min/avg/max/stddev: 54/54 153/200 459/1376 133/376][Risk: ** Self-signed Certificate **** Obsolete TLS version (< 1.1) **][TLSv1][JA3S: 623de93db17d313345d7ea481e7443cf][Issuer: C=AU, ST=Some-State, O=Internet Widgits Pty Ltd][Subject: C=AU, ST=Some-State, O=Internet Widgits Pty Ltd][Certificate SHA-1: DD:EB:4A:36:6A:2B:50:DA:5F:B5:DB:07:55:9A:92:B0:A3:52:5C:AD][Validity: 2019-07-23 10:32:39 - 2020-07-22 10:32:39][Cipher: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA]
- Binary executable download (this is how trickbot infects the PCs when people click on malspam links)
TCP 10.9.25.101:49197 <-> 185.98.87.185:80 [byte_dist_mean: 144.678397][byte_dist_std: 72.649105][entropy: 0.000000][total_entropy: 0.000000][score: 0.9990][proto: 7/HTTP][cat: Web/5][163 pkts/9113 bytes <-> 371 pkts/520336 bytes][Goodput ratio: 3/96][69.52 sec][Host: 185.98.87.185][bytes ratio: -0.966 (Download)][IAT c2s/s2c min/avg/max/stddev: 0/0 623/25 60010/4824 5733/276][Pkt Len c2s/s2c min/avg/max/stddev: 54/54 56/1403 204/1514 16/164][URL: 185.98.87.185/tablone.png[StatusCode: 200][ContentType: image/png][UserAgent: WinHTTP loader/1.0][Risk: ** Binary application transfer **][PLAIN TEXT (GET /tablone.png HTTP/1.1)]
- Known protocols (TLS) on non-standard ports
TCP 10.9.25.101:49464 <-> 170.238.117.187:8082 [byte_dist_mean: 71.693632][byte_dist_std: 36.108533][entropy: 4.780162][total_entropy: 20344.368866][score: 0.0085][proto: 7/HTTP][cat: Web/5][9 pkts/4738 bytes <-> 8 pkts/556 bytes][Goodput ratio: 89/22][59.19 sec][Host: 170.238.117.187][bytes ratio: 0.790 (Upload)][IAT c2s/s2c min/avg/max/stddev: 0/842 8335/9414 46230/46230 15705/18411][Pkt Len c2s/s2c min/avg/max/stddev: 54/54 526/70 1514/174 623/40][URL: 170.238.117.187:8082/ono19/BACHMANN-BTO-PC_W617601.AC3B679F4A22738281E6D7B0C5946E42/90[StatusCode: 0][ContentType: multipart/form-data][UserAgent: test][Risk: ** Known protocol on non standard port **][PLAIN TEXT (POST /ono)]
The above evidences are already enough to say that host 10.9.25.101 is doing something malicious that is worth to be analysed. However ntopng can help you do it more easily by means of the graphical interface and also because it enriches nDPI analysis with:
- Use of IP blacklists to identify compromised hosts.
- Malware anomaly score used to easily spot sources of trouble.
- Alert analysis accumulated per host, AS, network…
The same pcap can be ntopng analysed as follows
ntopng -i Downloads/Trickbot/2019-09-25-Trickbot-gtag-ono19-infection-traffic.pcap
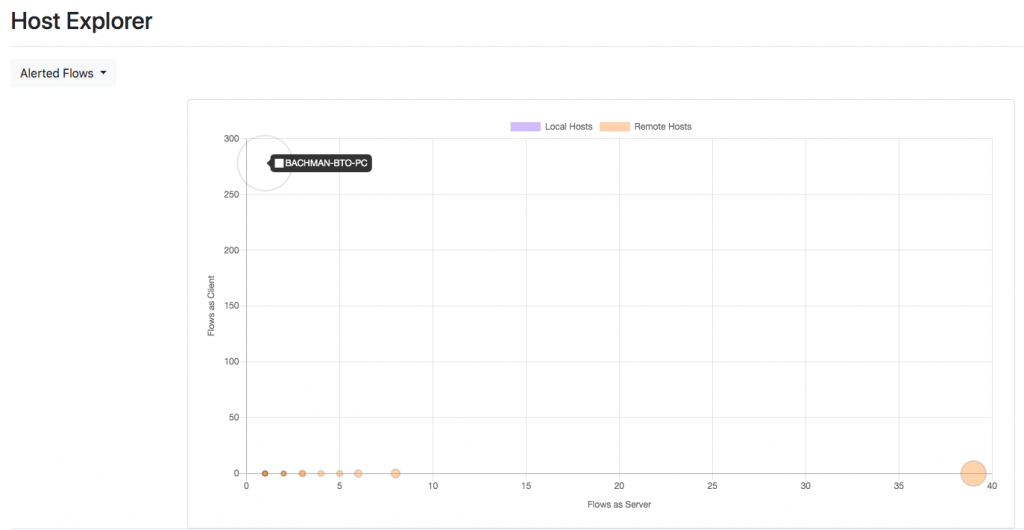
Going in the Hosts => Host Explorer page it is possible to select “Alerted Flows” to analyse hosts according to the number of alerted flows they have active. As you can see you can immediately realise that two hosts, BACHMAN-BTO-PC and 187.58.56.26 and the two outliers, and two suspicious hosts.
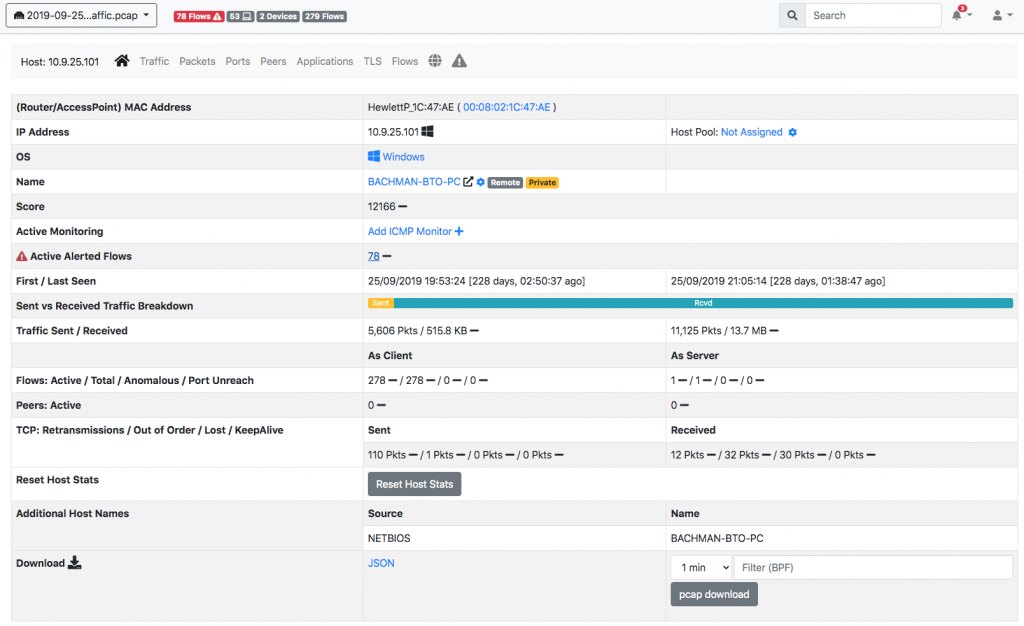
Clicking on BACHMAN-BTO-PC you can see that this host as a score of over 12’000 that is clearly an indication of security issues.
We also see that nDPI+ntopng reported binary file transfer and this is not a good news either.
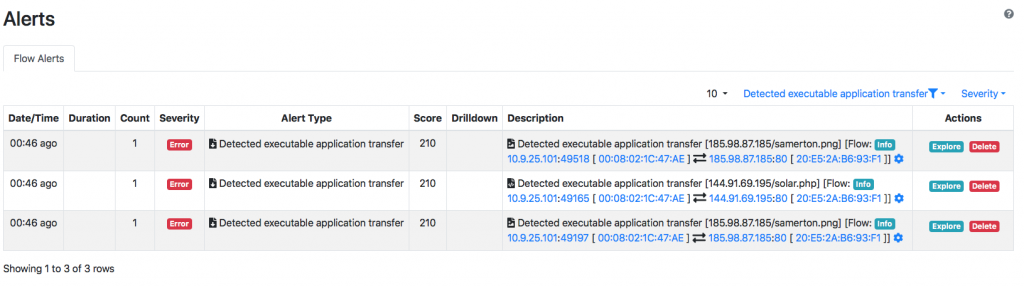
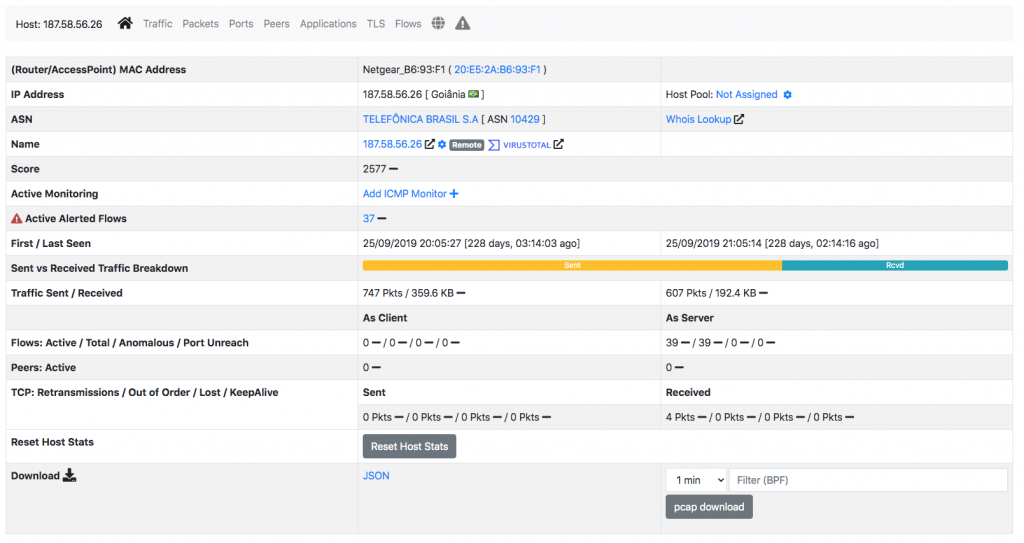
A very high score of over 2500 is also reported for the other host 187.58.56.26.
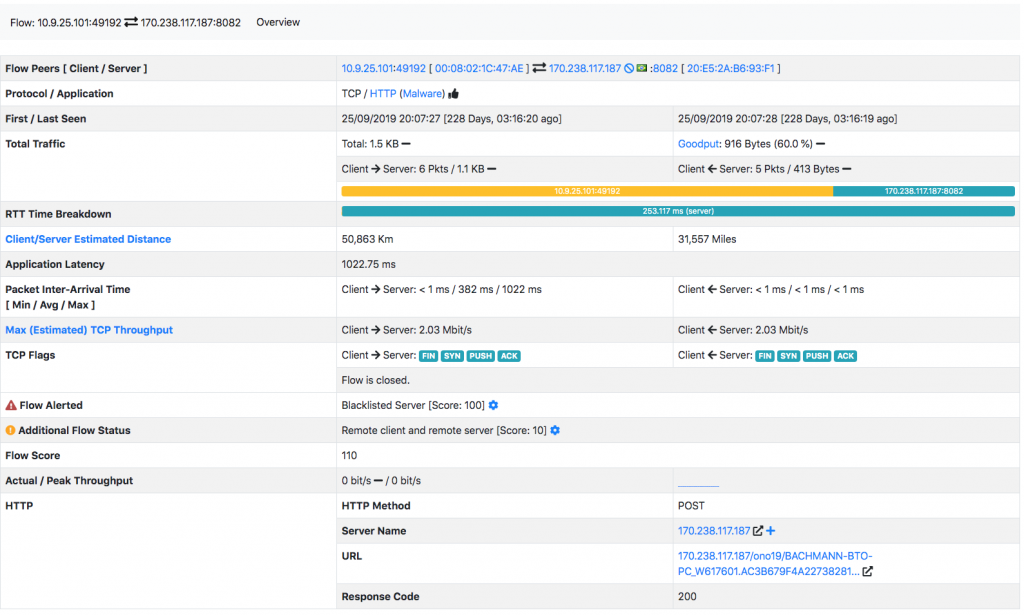
Exploring the host flows we see that out local infected host BACHMAN-BTO-PC is uploading data via HTTP to 170.238.117.187
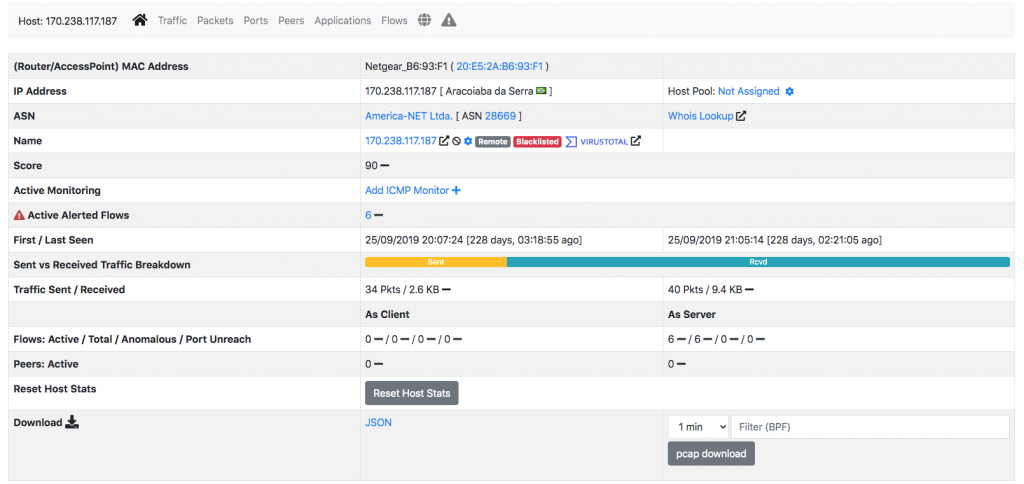
This looks even more suspicious. Let’s analyse this host that is very bad as ntopng marks it as blacklisted, being his IP listed on a blacklist ntopng has accessed (see this page for learning more about ntopng blacklists).
In order to complete our investigations, let’s check the reputation of this host 170.238.117.187 by clicking on the VirusTotal icon that bring us to this page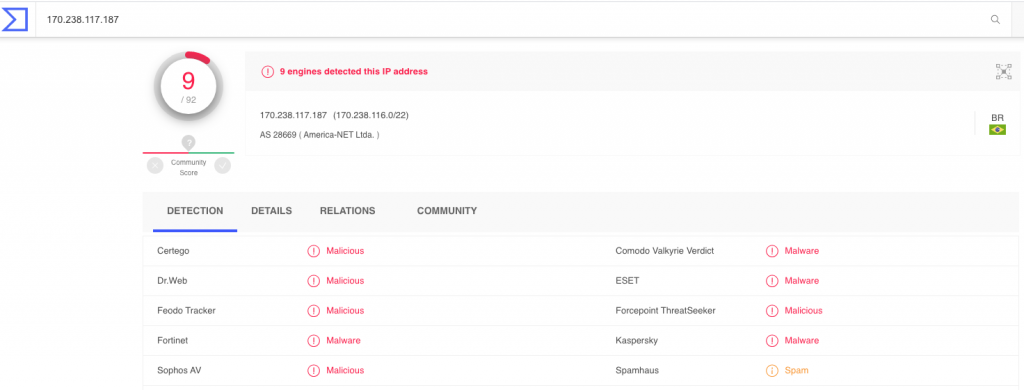
Our analysis is over. We have identified the local infected host, and where it is uploading our files.
Are you interested in knowing more about nDPI and traffic analysis? You can join us this week, May 14th 14:30 CET at RIPE 80. The presentation will be delivered from remote: just register for the RIPE meeting and enjoy it from wherever you are.
Enjoy analysing malware network traffic with nDPI and ntopng.