One of the greatest strengths of ntopng is its ability to correlate data originating at different layers and at multiple sources together. For example, ntopng can look at IP packets, Ethernet frames and, at the same time, poll SNMP devices. This enables ntopng to effectively perform correlations and observe:
- The behavior of IP addresses (e.g., Is this IP known to be blacklisted?)
- The MAC addresses carrying IP traffic around in the network
- The physical location of the MAC addresses (i.e., physical switches traversed by a given MAC address along with trunk and access ports)
ntopng, starting from version 4.1, capitalizes on this information to implement attack mitigation via SNMP. In other words, ntopng:
- Uses an indication of compromise known as score to determine whether an IP is an attacker (client score) or a victim (server score).
- Finds physical switches and access ports where attackers are connected to.
- Uses SNMP to turn access ports down, thus effectively disconnecting the attackers from the healthy network.
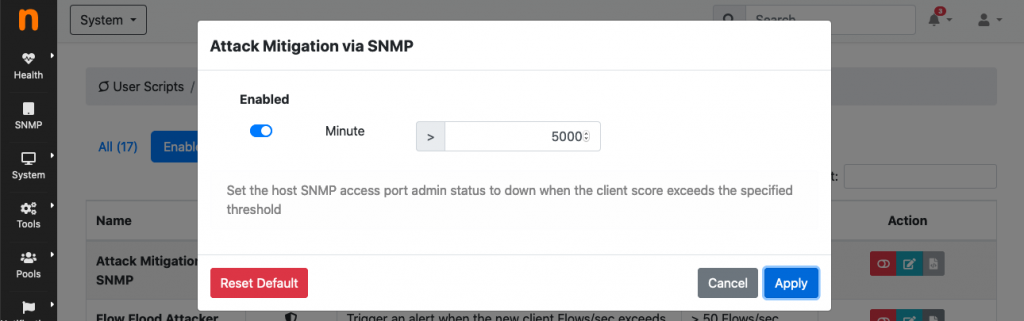
Attack mitigation via SNMP is implemented as an ntopng plugin available in versions Enterprise M and above, and can be enabled from the user scripts configuration page
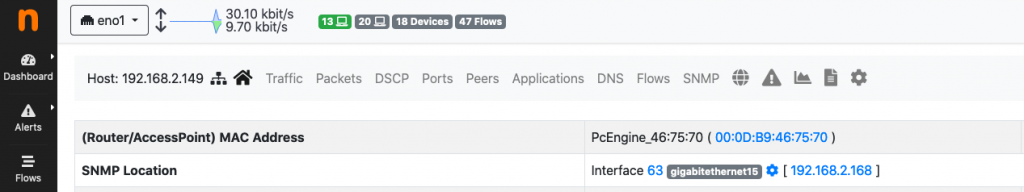
Let’s see what happens in practice. For this example, an attacker host 192.168.2.149 is configured to run a port scan (nmap -sS) towards 192.168.2.222. ntopng, using traffic and SNMP data is able to identify host 192.168.2.149 as a PcEngines connected to interface gigabitethernet15 of switch 192.168.2.168.
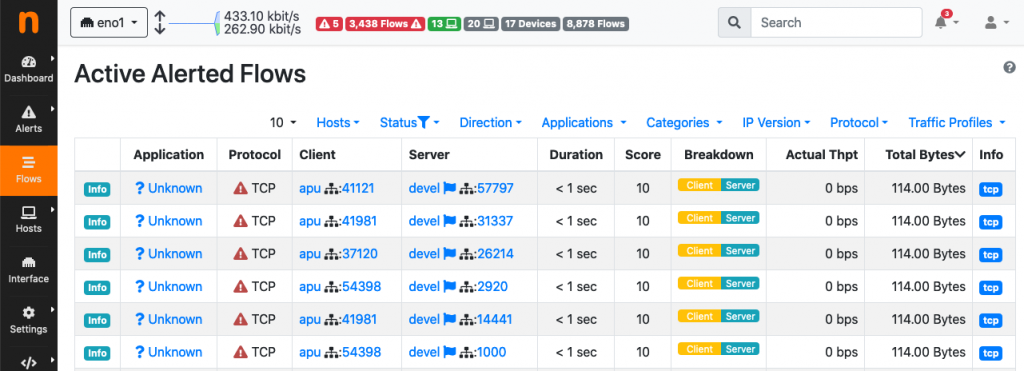
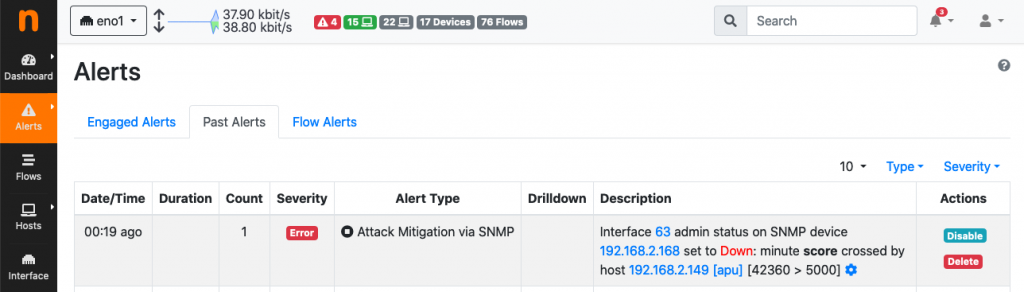
The port scan is immediately detected by ntopng
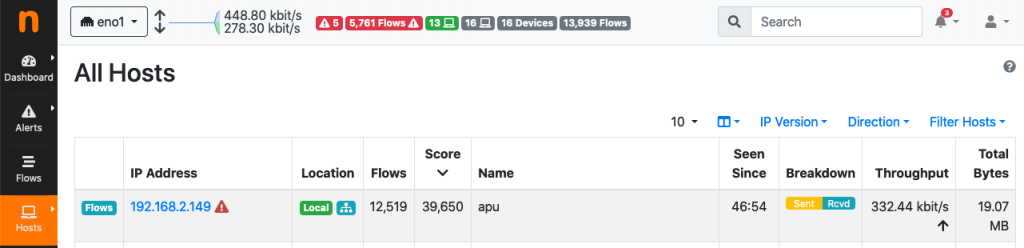
Indeed, there are many alerted “TCP Connection Refused” flows having 192.168.2.149 as source – apu is the DNS name of 192.168.2.149. Due to this suspicious activity, there is a significant increase in the score of 192.168.2.149
This score is high enough to ensure the attack mitigation via SNMP kicks in. Within a minute from the increase in the host score, mitigation causes the port on the SNMP device to be turned down
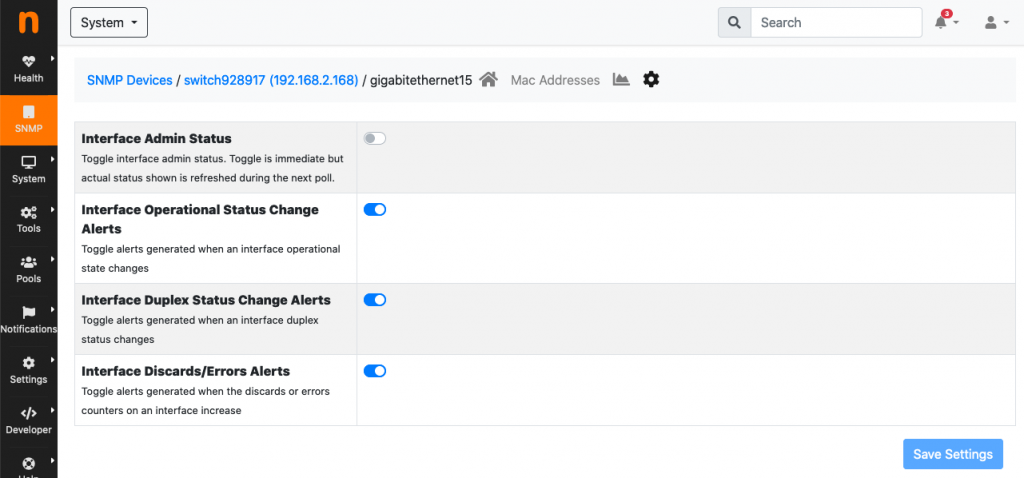
From this point on, attacker host 192.168.2.149 is effectively disconnected from the network and, thus, it becomes harmless. It is up to the network administrator now to intervene and do any necessary cleanup operation on the attacker host. Once the issues have been resolved, the SNMP port can be turned up again from the preferences.
Having attack mitigation via SNMP implemented in ntopng is just a preliminary step towards making ntopng not just a monitoring and visualisation tool but also something which proactively prevents attackers from harming the network.
What’s next is the ability to protect a network by mitigating external attackers. nScrub is a good example of a tool that can mitigate DDoS attacks. Stay tuned for news !